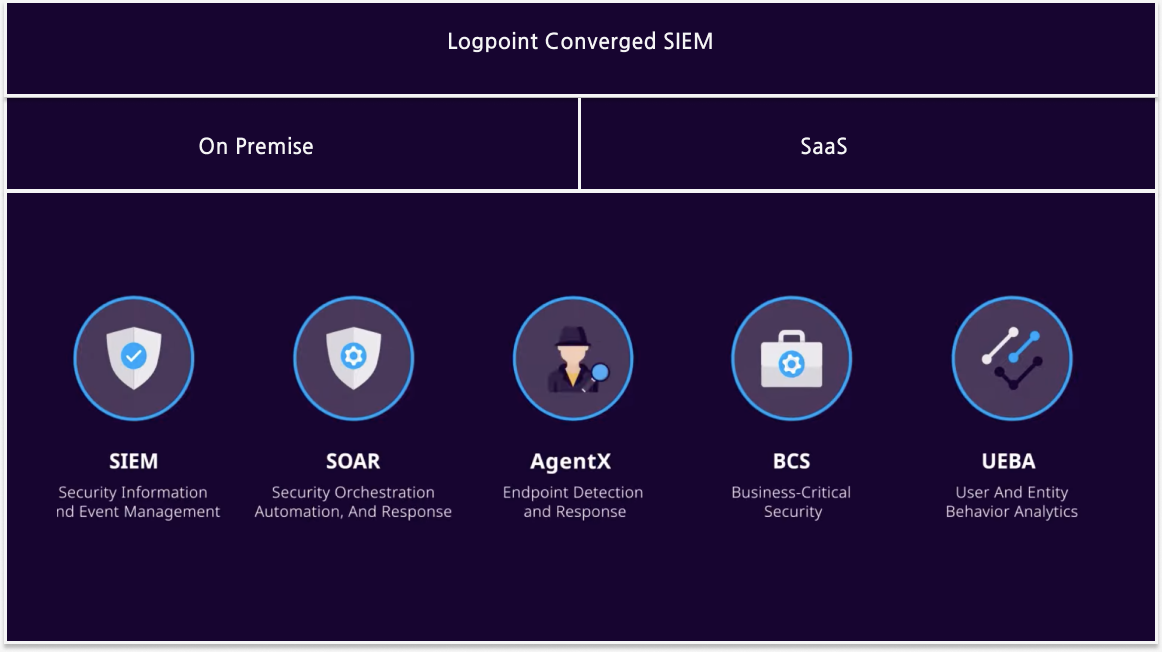
Logpoint Converged SIEM combines SIEM (Security Information and Event Management), UEBA (User and Entity Behavior Analytics), SOAR (Security Orchestration Automation and Response), BCS (Business Critical Security), and Endpoint Detection and Response via a unified platform. It is available as a SaaS and an on-premise deployment.
It collects real-time data from multiple sources and centralizes it for comprehensive analysis. You can easily search, analyze, generate reports, detect vulnerabilities, and configure alerts to enhance threat detection capabilities. You can also automate threat response based on specific security incidents.
Logpoint SIEM serves as a central hub for security event data within an organization. It collects, correlates, analyzes, and visualizes data from various sources, empowering security teams to detect and investigate security incidents quickly. Logpoint SIEM’s reporting and historical data analysis capabilities ensure compliance with regulations and facilitate continuous improvement of an organization’s security needs.
Logpoint SIEM provides organizations with the following capabilities:
Raw logs are collected or fetched from log sources and split into individual messages. Logpoint adds contextual and domain information to the messages by normalizing, enriching and labelling them.
Enriches logs with information gathered from a variety of threat intelligence providers.
Customizable dashboards and widgets help you monitor and visualize your logs. You can also perform historical or real-time data searches.
Alert Rules check when a specific query and its conditions match a defined activity that correlates to a potential threat or vulnerability within the logs. If they do, an alert is generated in addition to an incident correlating to the alert. You can use the incident to investigate whether there is a real threat or not.
Reports are made up of a sequence of search queries that visualize the data in different ways. Report Templates contain the search queries while template layouts controls a report’s look and feel. Logpoint has a number of out-of-the-box vendor reports that can be used as-is or further customized. You can schedule reports to run automatically, in a variety of formats and sent to specific users.
Security Orchestration, Automation, and Response automates processes based on SIEM-based incidents. You can use SOAR playbooks to automate processes based on incidents that are rare or incidents that happen often.
Logpoint AgentX is designed to facilitate the transfer of logs and telemetry from various endpoints, including servers, workstations, and applications, to allow Logpoint Converged SIEM to perform comprehensive data analysis and precise detection capabilities for malware. AgentX also integrates seamlessly with Logpoint SOAR to enable security teams to perform automated real-time investigation and remediation of threats directly on the endpoints.
Detect and respond to threats to your SAP landscape through dedicated SIEM-based SAP extractors.
Detects risks and behavioral anomalies using machine learning. UEBA uses 30-days of user and entity behaviour to create a baseline. New activity is compared to this baseline and a risk score is generated. Based on the risk score an incident can be generated, the behavior investigated or a SOAR playbook is triggered.
We are glad this guide helped.
Please don't include any personal information in your comment
Contact Support