The Intelligence Card page summarizes all the threat information fetched and analyzed by Recorded Future on the selected entity.
You can find the Intelligence Cards of the following entity types:
IP Address
URL
Domain
Hash
Vulnerability
The following section describes the components found in the Intelligence Card page.
The Overview tab summarizes the risk information, including Recorded Future risk score and triggered risk rules of the selected entity.
The top of the Overview tab displays the entity that you have drilled forward from the search results.
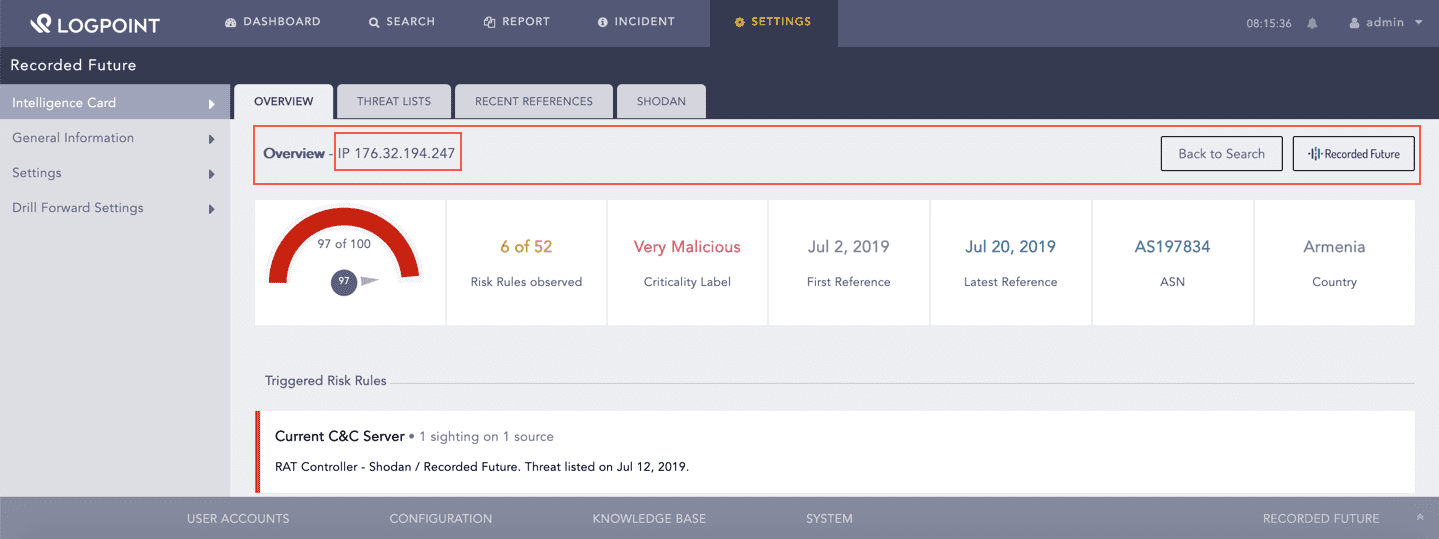
Selected Entity¶
The Back to Search option redirects you to the search results page.
Back to Search¶
The Recorded Future option redirects you to Recorded Future’s Intelligence Card.
Recorded Future has its own set of risk rules that are triggered on the basis of the risk rule evidence found in different sources. The sources include threat feeds and IP reputation lists, security research blogs, social media posts, paste sites, underground forums, and malware analysis services. You can find the triggered risk rules and their details under the Triggered Risk Rules section.
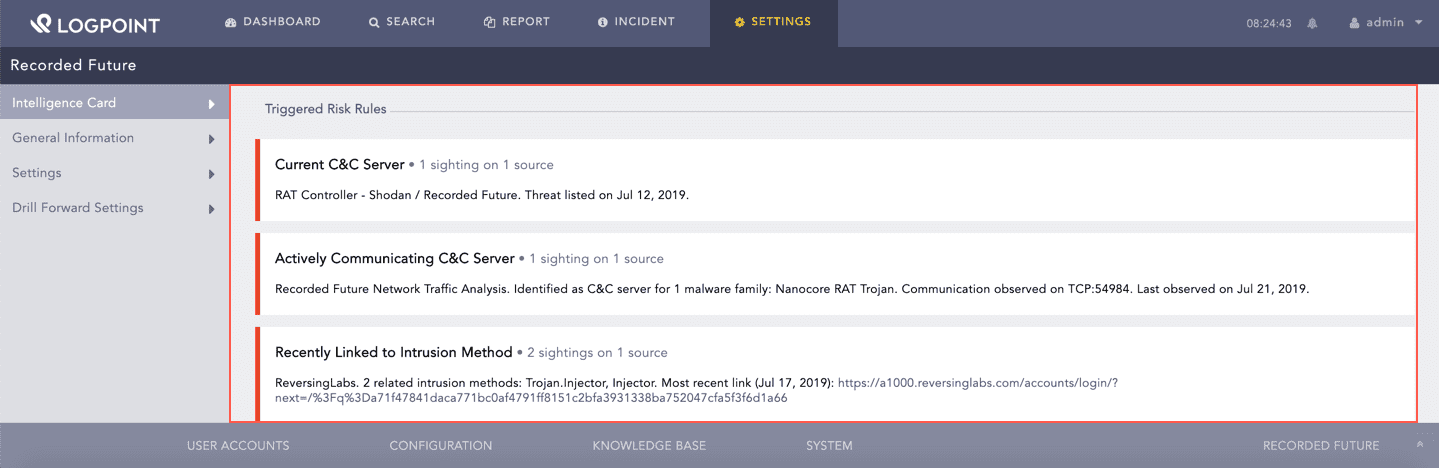
Triggered Risk Rules¶
The Threat Lists tab consists of the lists created by Recorded Future. It creates the list by analyzing its threat intelligence, and collection of threat lists and the whitelists published in the external community. You can find the threat lists for the selected entity under Threat Lists.
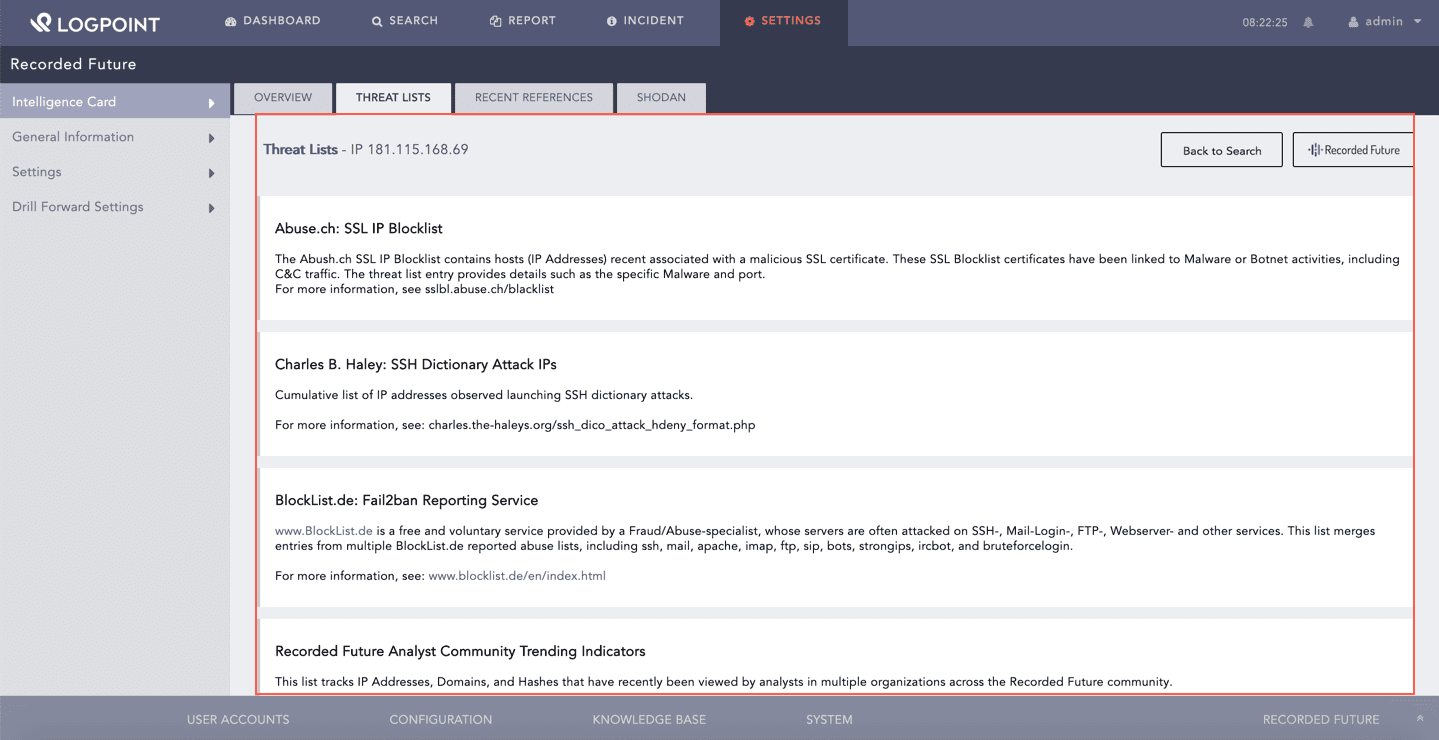
Threat Lists¶
The Recent References tab consists of entity references in external sources. These sources include cyber events, paste sites, social media, information security sources, underground forums, and dark web sources. The Recent References section displays the following information for each reference:
Type
Title
Source
Published
Fragment
URL
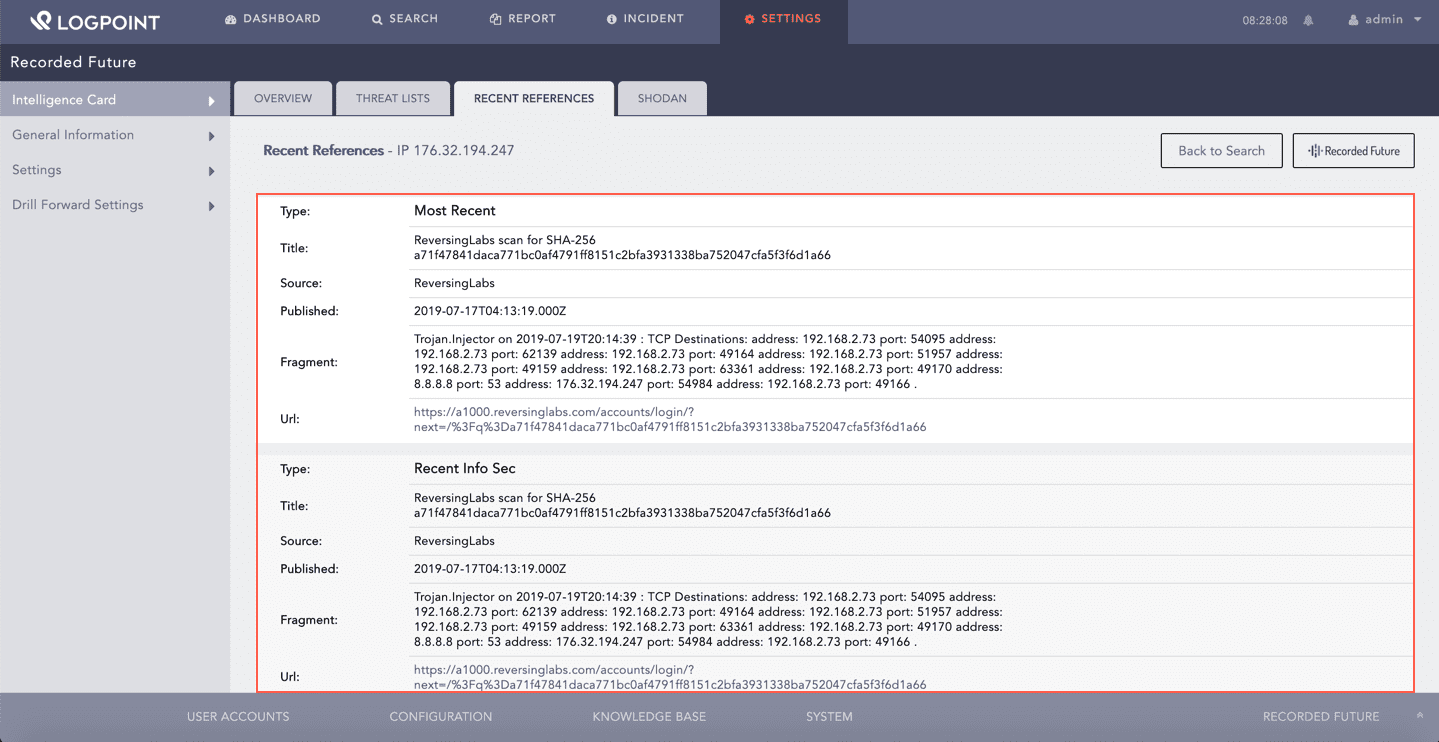
Recent References¶
Shodan is a search engine for internet-connected devices that enriches the IP Address and Vulnerability Intelligence Cards with its fetched data. Shodan enriches the IP Address Intelligence Card with the following data:
Country
Organization
Operating system
ISP
Last update date
Autonomous system number (ASN)
Known vulnerabilities
Device use tags
Ports
Shodan also displays the geographic location of an IP address in a map.
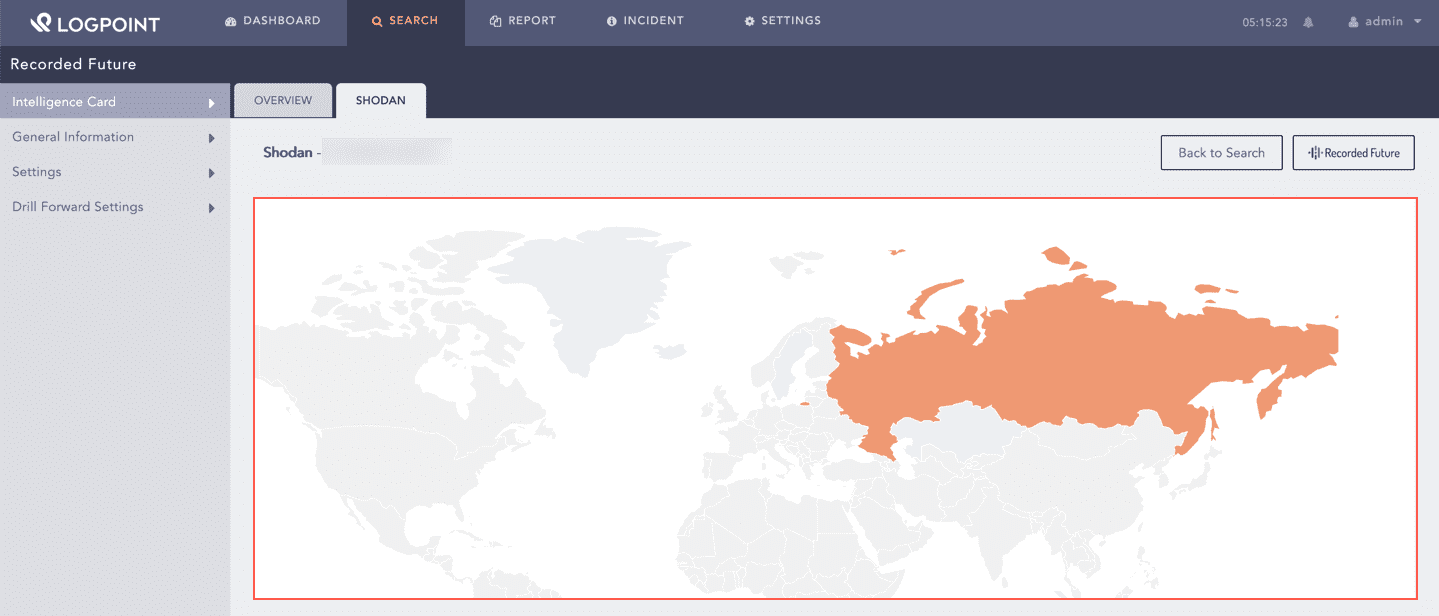
Map¶
You can find the enriched data for the IP address under General Information, Tags, and Ports.
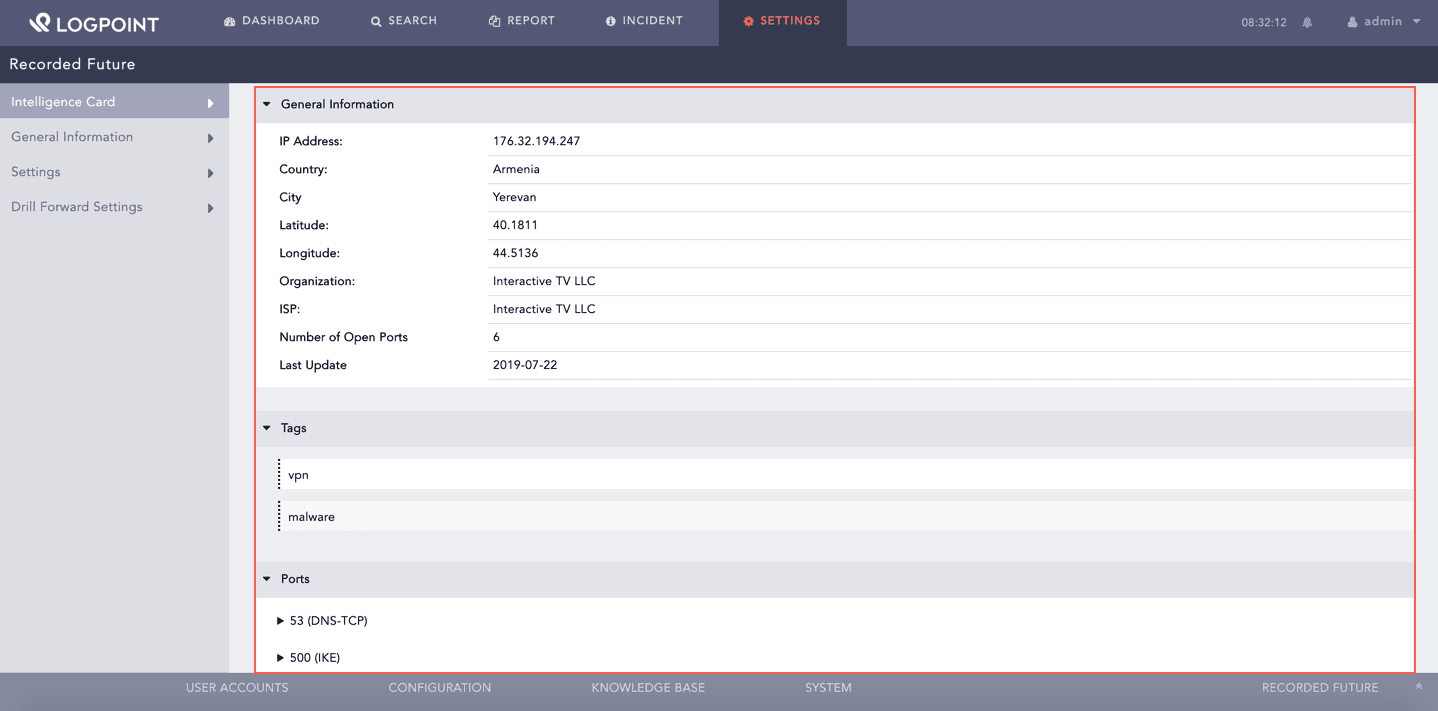
Enriched Data for IP Address¶
Shodan enriches the Vulnerability Intelligence Card with fetched data from the Exploit Database. You can find the enriched data under the Exploits section.
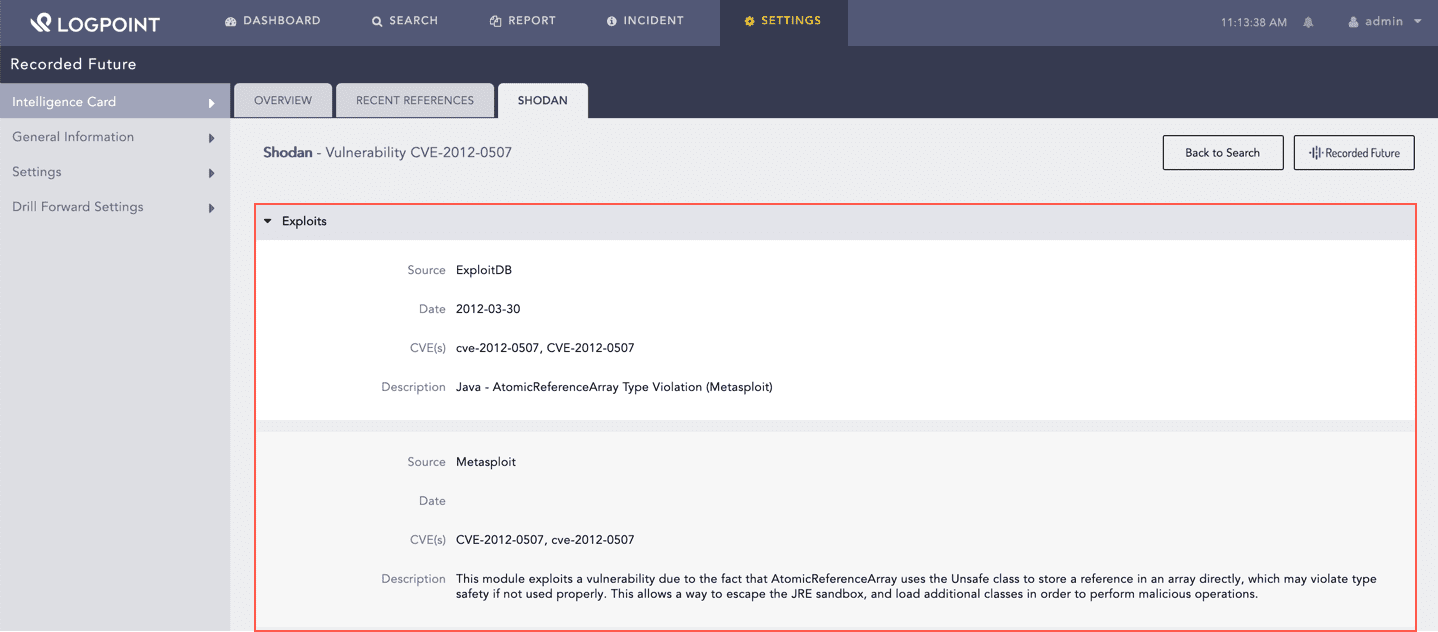
Enriched Data for Vulnerability¶
We are glad this guide helped.
Please don't include any personal information in your comment
Contact Support