You can find the summary of the threat information fetched, enriched and analyzed by Recorded Future on the selected entity in Intelligence Card.
There are Intelligence Cards for the following entity types:
IP Address
URL
Domain
Hash
Vulnerability
To access an intelligence card:
Search for the enriched logs.
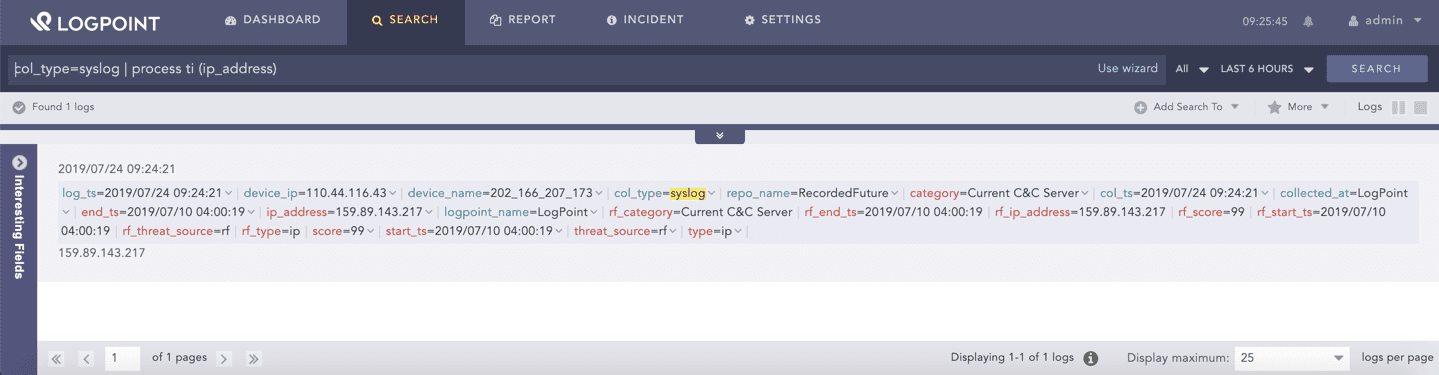
Search Tab¶
Click the drop-down of the previously mapped field from Drill Forward Settings.
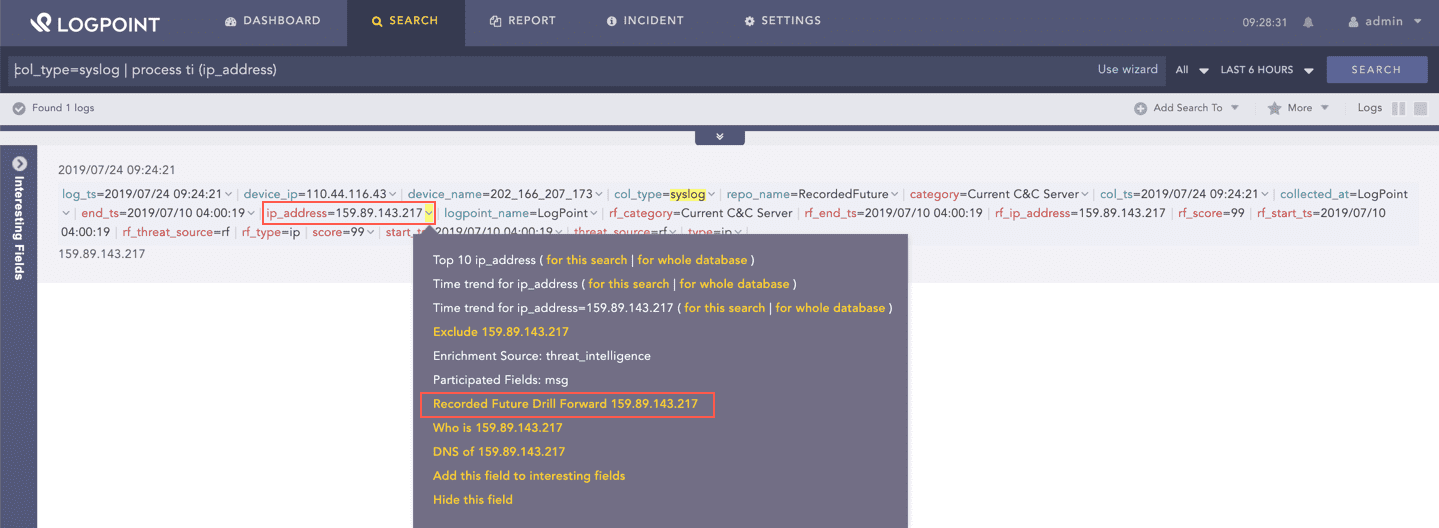
Recorded Future Drill Forward¶
Click Recorded Future Drill Forward.
Note
Each drill forward uses 1 API credit.
Recorded Future redirects you to the Intelligence Card.
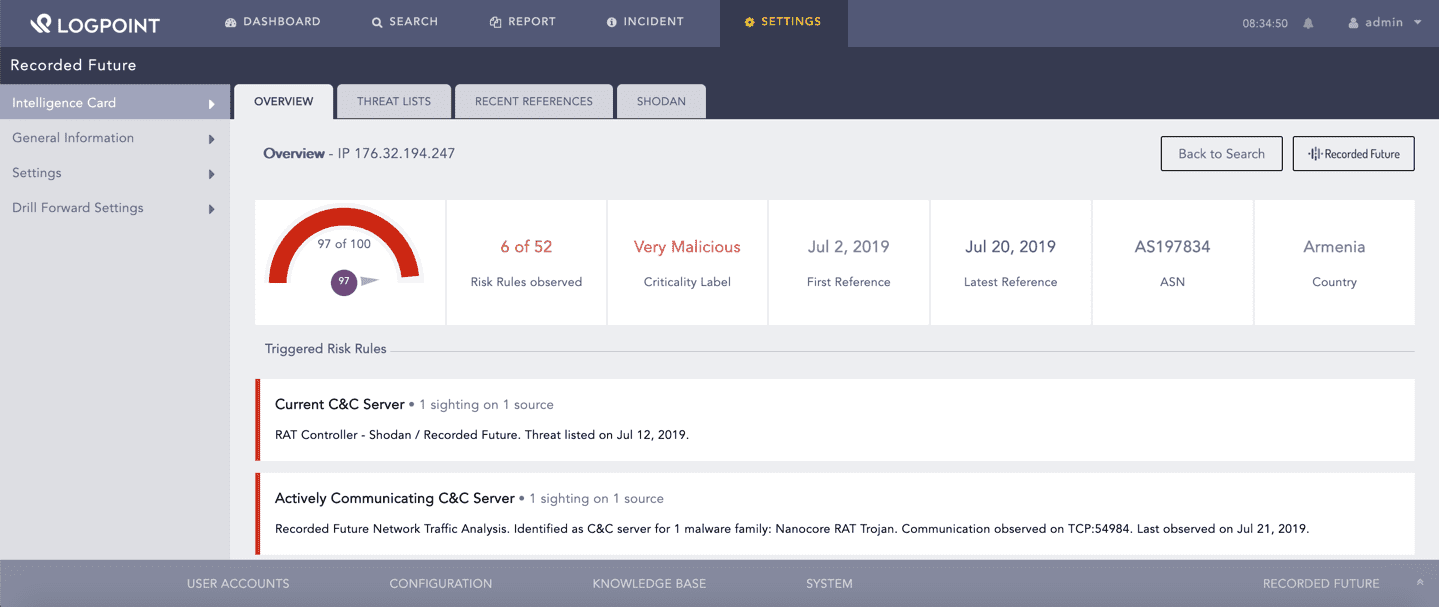
Intelligence Card¶
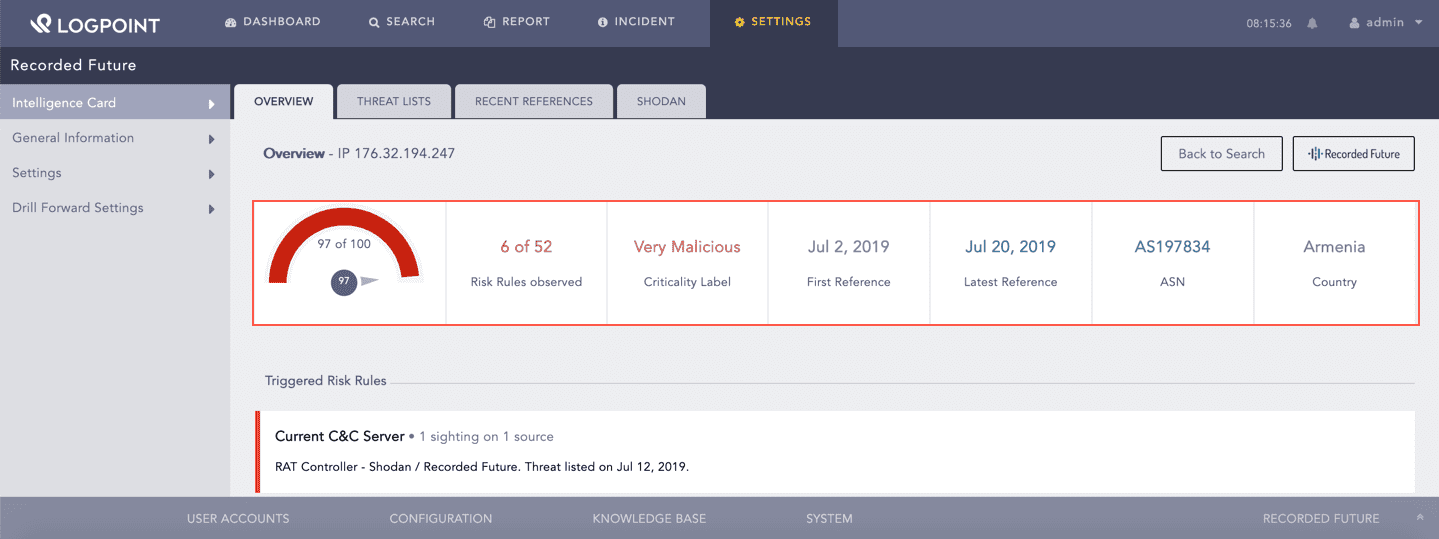
You can find the risk information summary, including the Recorded Future risk score and triggered risk rules of the selected entity in Overview. Risk score is a numerical value that represents the level of risk associated with the entity. Triggered Risk Rules are a set of automated alerts for specific types of security risks that are customized to look for risks across multiple data sources.
You can click Back to Search to redirect you to the search results page and Recorded Future to the Recorded Future’s Intelligence card.
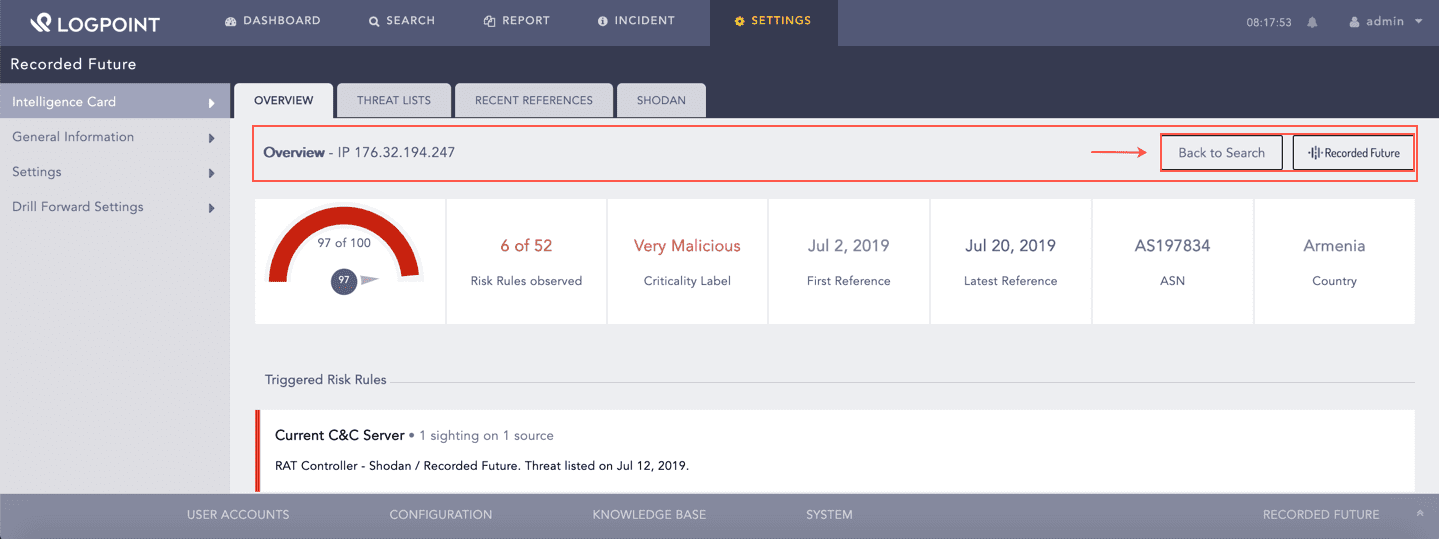
Back to Search¶
Recorded Future generates the risk score by analyzing the level of risk on the entity. It analyzes risks based on its set of risk rules and threat lists. Each risk rule has a criticality, a criticality label and a risk score. The risk rule is color-coded by the criticality of the threat. The gauze chart is used to display the risk score of the entity.
Criticality Label |
Criticality |
Risk Scores |
Color |
|---|---|---|---|
Very Malicious |
4 |
90-99 |
Red |
Malicious |
3 |
65-89 |
Red |
Suspicious |
2 |
25-64 |
Bright Yellow |
Unusual |
1 |
5-24 |
Light Gray |
No current evidence of risk |
0 |
0 |
Light Gray |
You can find the number of triggered risk rules and their severity level in Risk Rules observed and Criticality Label. The date when the risk rule was first triggered is displayed in First Reference, and the date it was last triggered is displayed in Latest Reference. You can also find the autonomous system numbers (ASN) and the country where the threat is detected. Autonomous System Numbers (ASN) are unique identifiers of each network on the internet.
Risk Score and Risk-Related Content¶
Recorded Future has its own set of risk rules that are triggered based on the risk rule evidence found in different sources. The sources include threat feeds, IP reputation lists, security research blogs, social media posts, paste sites, underground forums and malware analysis services. You can find the triggered risk rules and their details under Triggered Risk Rules.
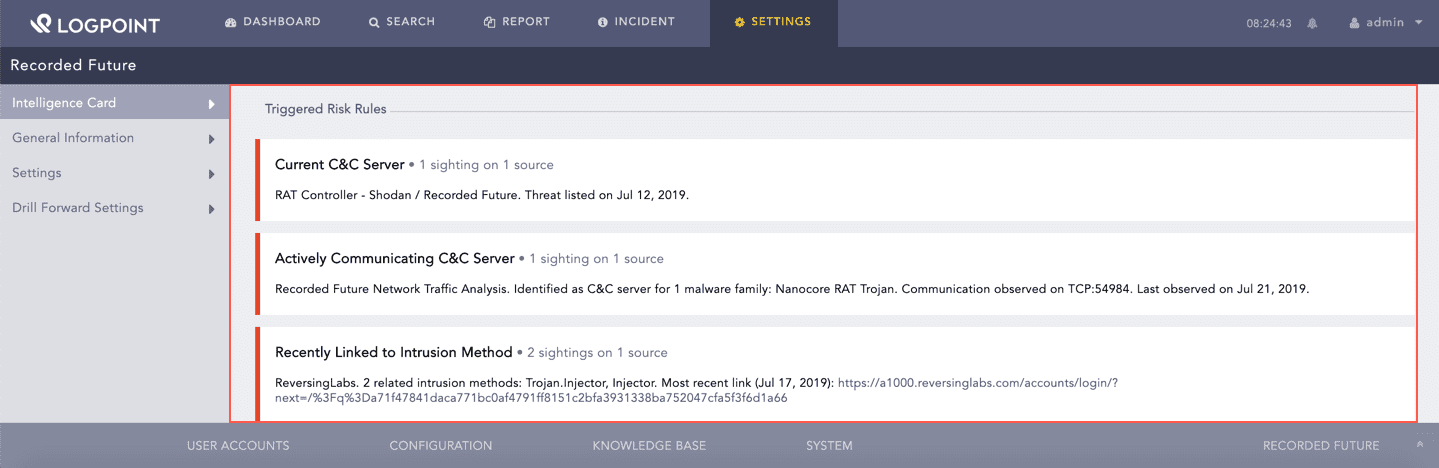
Triggered Risk Rules¶
You can find the threat lists for the selected entity in Threat Lists. It is a collection of information and analysis about specific cyber threats, such as malware, phishing campaigns and vulnerabilities.
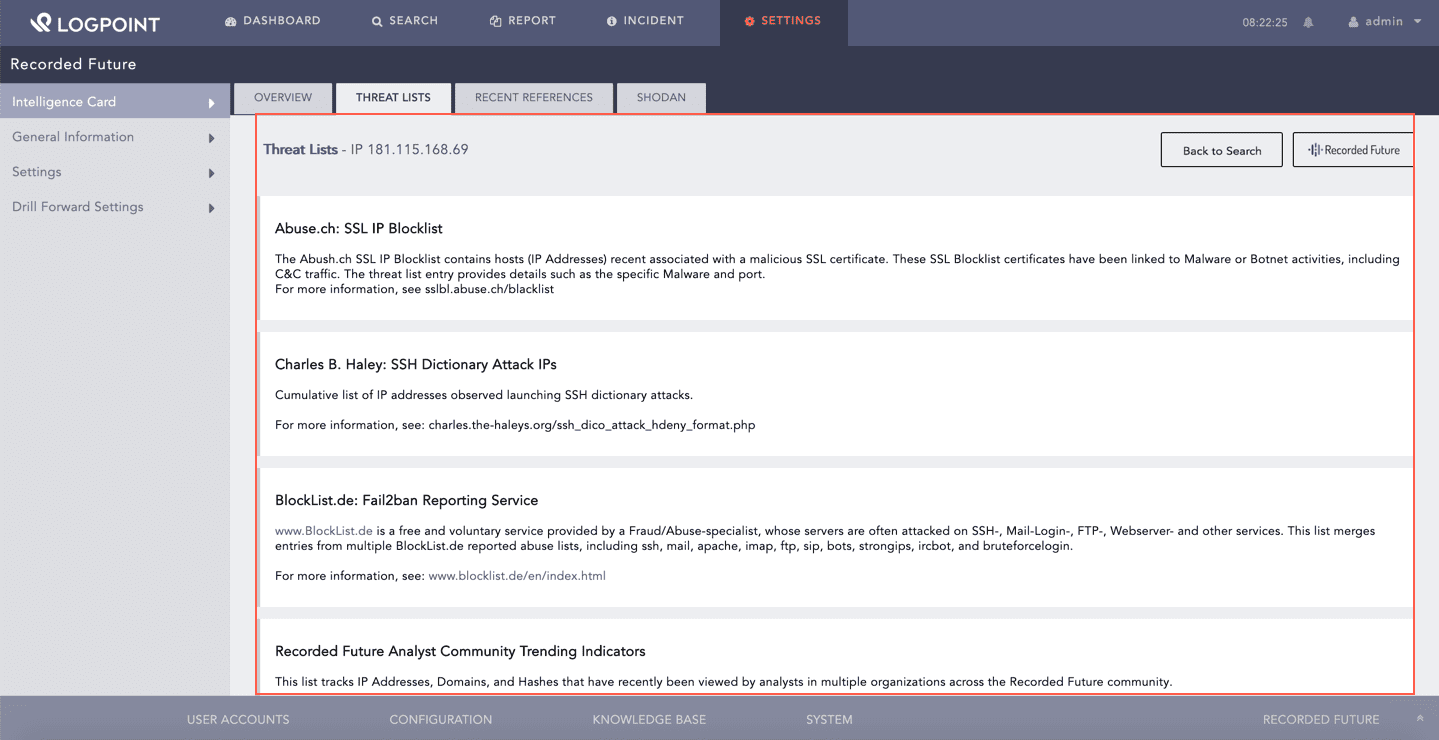
Threat Lists¶
You can find the recent mentions of the selected entity in various sources including but not limited to News, Blogs, Social Media and Dark Web in Recent References.
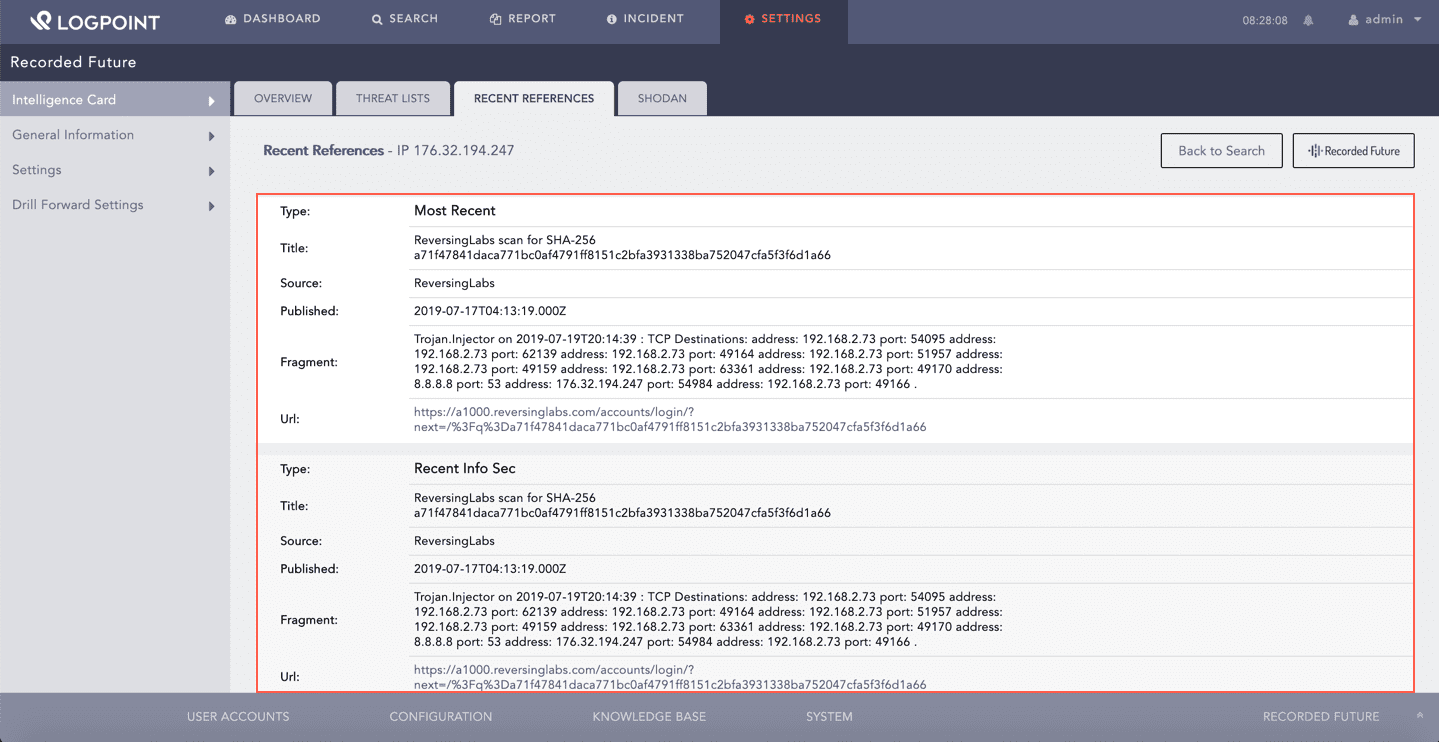
Recent References¶
Shodan is a search engine for internet-connected devices that enriches the IP Address and Vulnerability Intelligence Cards with its fetched data. Shodan enriches the Vulnerability Intelligence Card with fetched data from the Exploit Database. You can find the enriched data in Exploits.
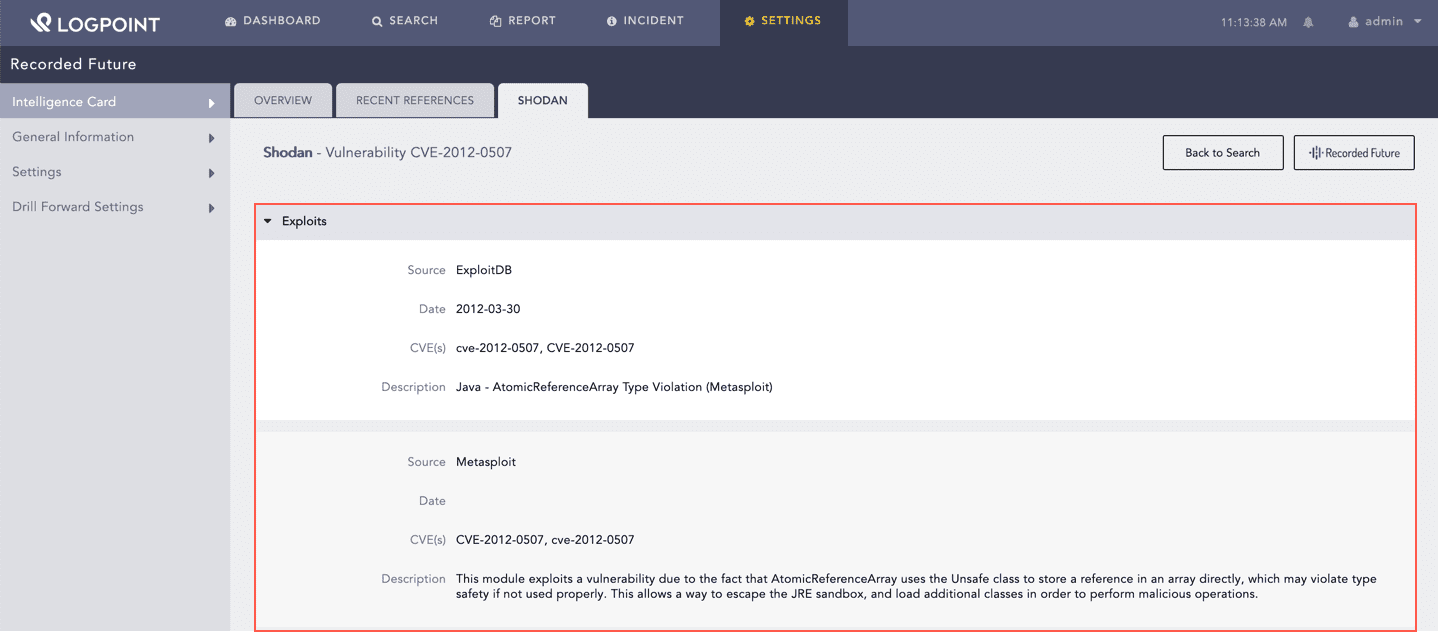
Enriched Data for Vulnerability¶
Shodan enriches the IP Address Intelligence Card with the following data:
Country
Organization
Operating system
ISP
Last update date
Autonomous system number (ASN)
Known vulnerabilities
Device use tags
Ports
You can find the geographic location of the IP address on a map and further enriched data in General Information, Tags and Ports.
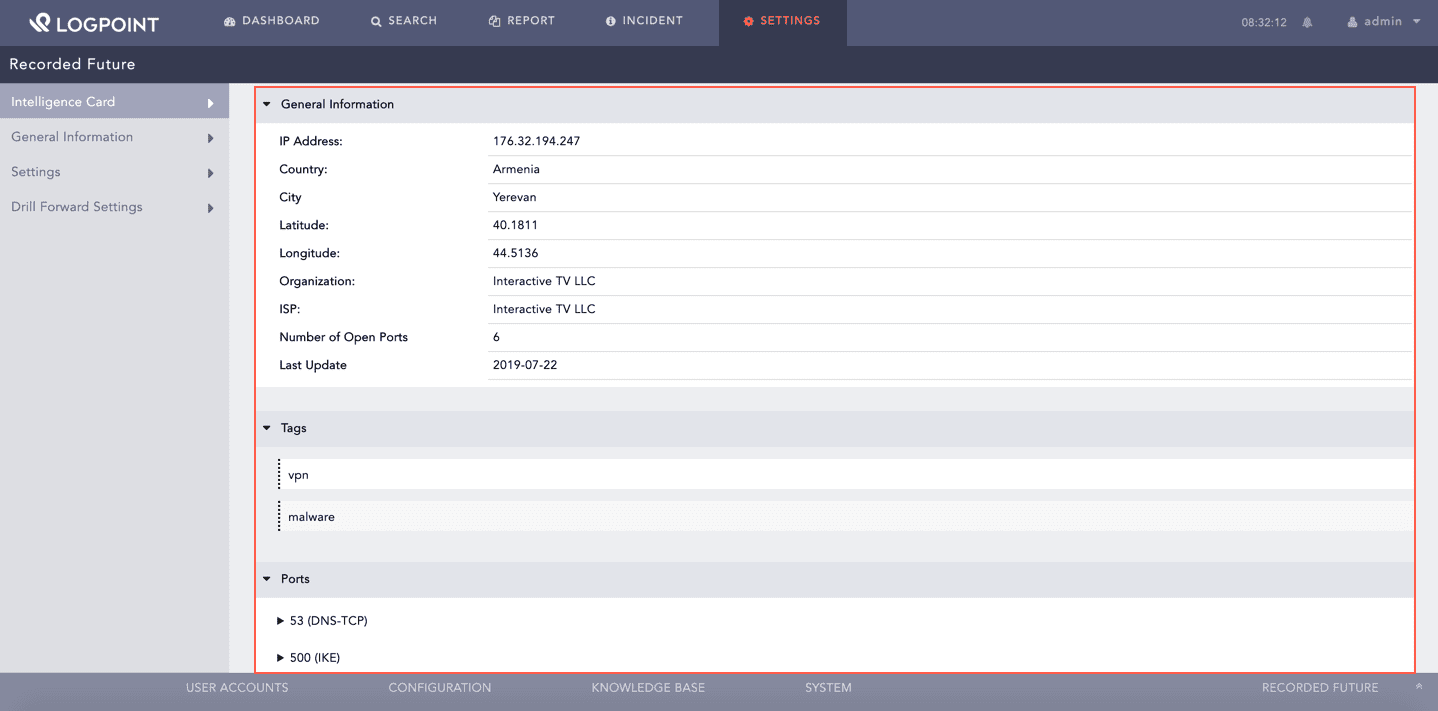
Enriched Data for IP Address¶
We are glad this guide helped.
Please don't include any personal information in your comment
Contact Support