Trigger Condition: The UEBA module detects exfiltration with a high-risk score.
Query:
norm_id=UEBA (threat="Possible Exfiltration" OR threat ="Potential Data Theft") event_category=anomaly
Trigger Condition: The UEBA module detects collection with a high-risk score.
Query:
norm_id=UEBA threat="Possible Collection" event_category=anomaly
Trigger Condition: The UEBA module detects credential access with a high-risk score.
Query:
norm_id=UEBA threat="Possible Credential Access" event_category=anomaly
Trigger Condition: The UEBA module detects defense evasion with a high-risk score.
Query:
norm_id=UEBA threat="Possible Defense Evasion" event_category=anomaly
Trigger Condition: The UEBA module detects discovery with a high-risk score.
Query:
norm_id=UEBA threat="Possible Discovery" event_category=anomaly
Trigger Condition: The UEBA module detects execution with a high-risk score.
Query:
norm_id=UEBA threat="Possible Execution" event_category=anomaly
Trigger Condition: The UEBA module detects impact activity with a high-risk score.
Query:
norm_id=UEBA threat="Possible Impact" event_category=anomaly
Trigger Condition: The UEBA module detects initial access with a high-risk score.
Query:
norm_id=UEBA threat="Possible Initial Access" event_category=anomaly
Go to Reports >> Report Templates >> VENDOR REPORT TEMPLATES.
Click Add from Actions.
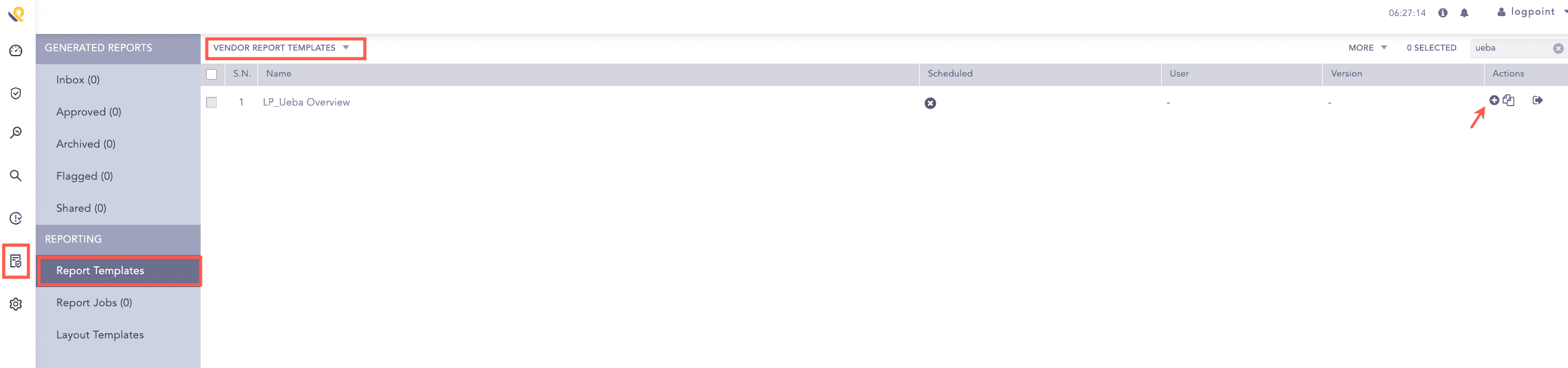
Adding LP_Ueba Overview¶
Click Run this Report from Actions.
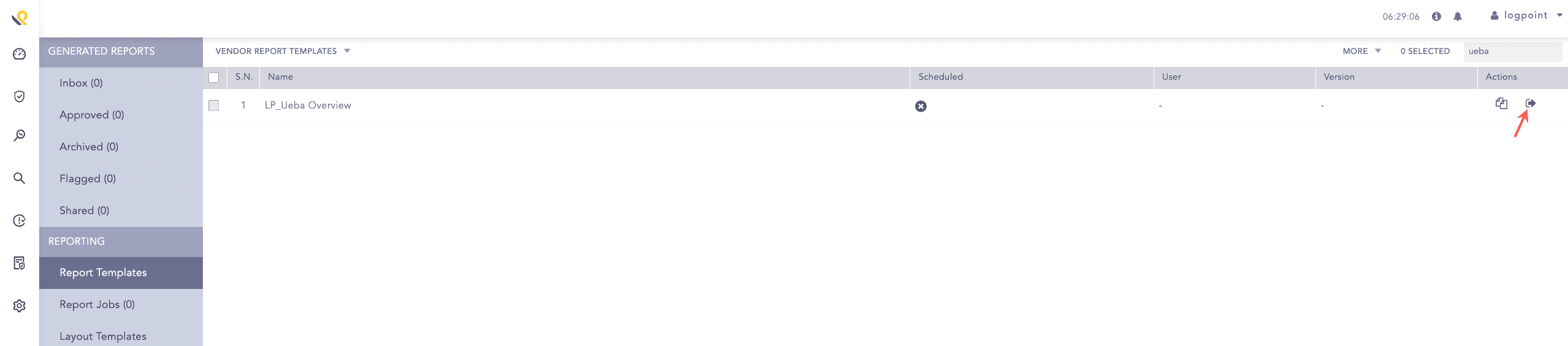
Running LP_Ueba Overview¶
Select Repos, Time Zone, Time Range, Export Type, and enter the Email address.
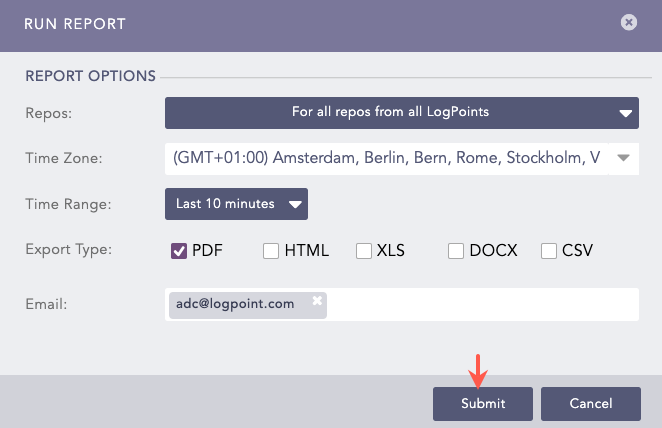
Running Report¶
Click Submit.
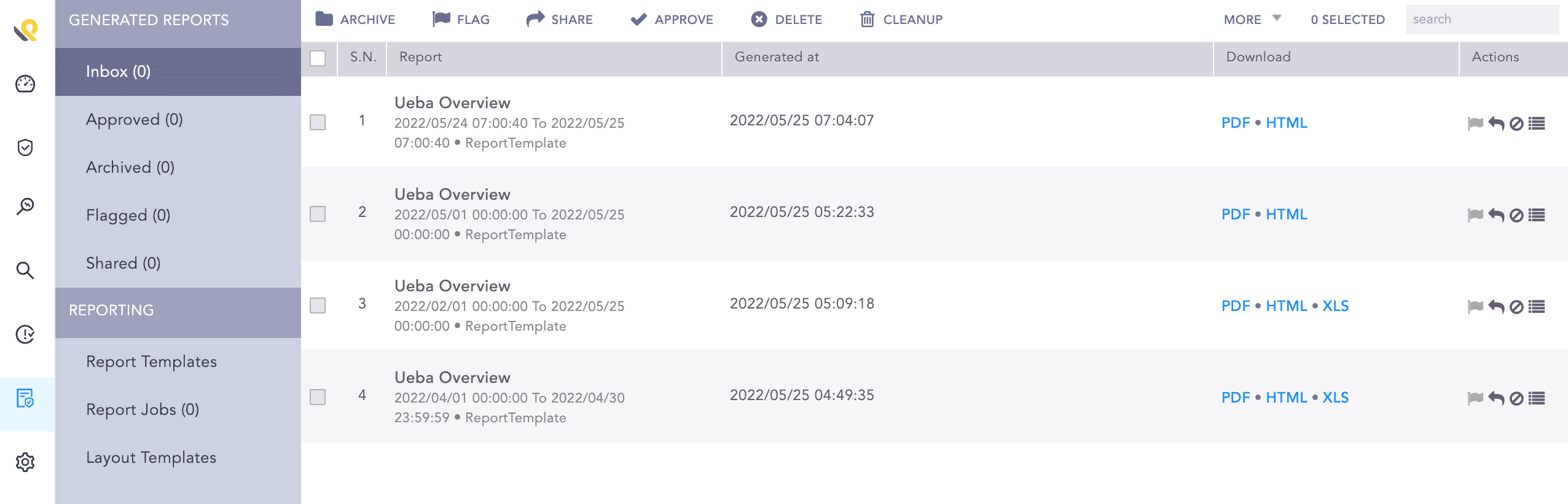
Generated Reports¶
You can view the reports being generated under Report Jobs and download the generated reports from Inbox with .pdf or .html extension by clicking PDF or HTML under the Download section.
A report contains widgets enabling you to analyze the data in different forms like graphs, time trends, lists, and text. Reports are time-bound, which means they are incident summaries over a period of time, for example, the last 24 hours or last five minutes. While generating a report, you can customize the calendar period based on your requirements.
The LP_Ueba Overview report provides:
An overview of the risk distribution (Extreme, High, Medium, and Low) detected by LogPoint.
An overview of the risk distribution (Extreme, High, Medium, and Low) by Possible Defense Evasion, Possible Exfiltration, Possible Collection, Possible Execution, Possible Initial Access, Possible Credential Access, Possible Impact, and Possible Discovery.
In the case of risk distribution:
Risk Level |
Risk Count |
|---|---|
Extreme |
Above 74. |
High |
Below 74 and above 49. |
Medium |
Below 50 and greater than 24. |
Low |
Below 25. |
We are glad this guide helped.
Please don't include any personal information in your comment
Contact Support