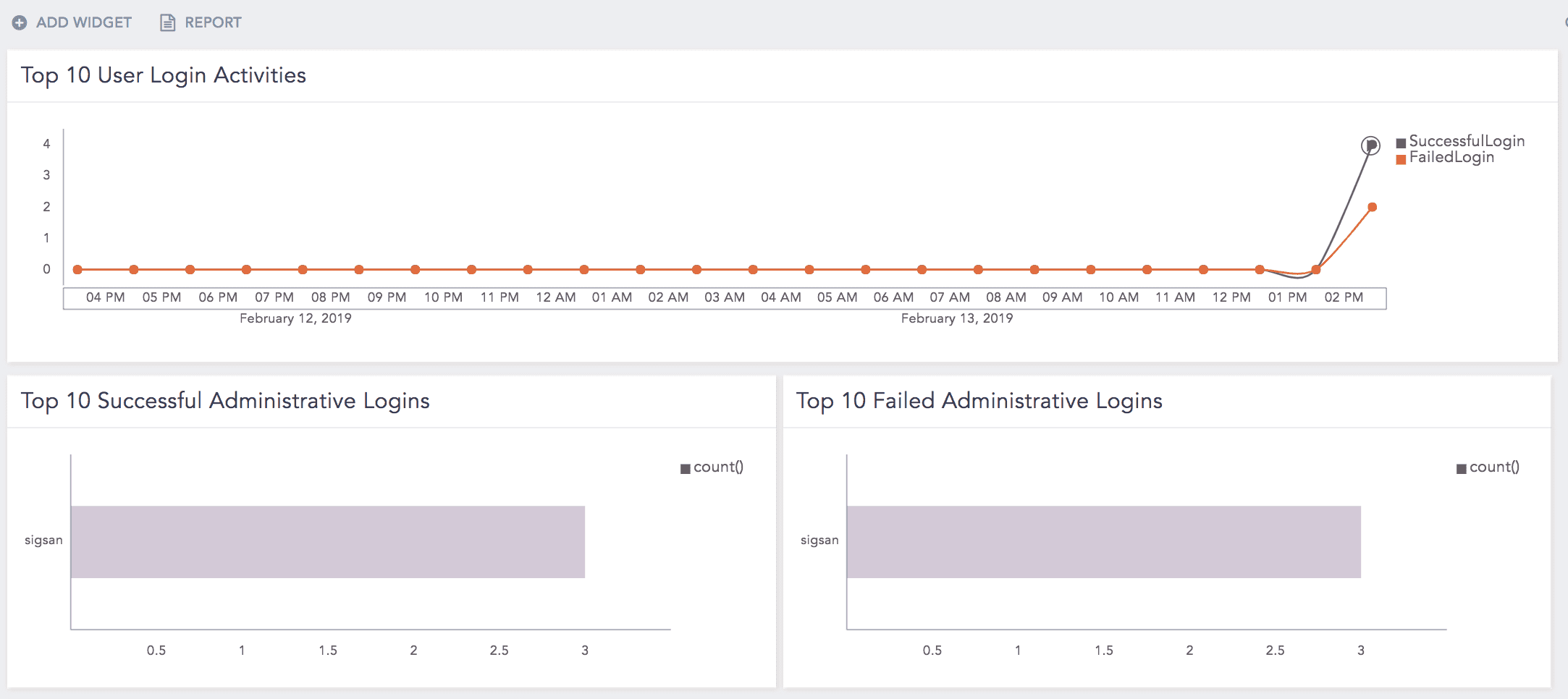
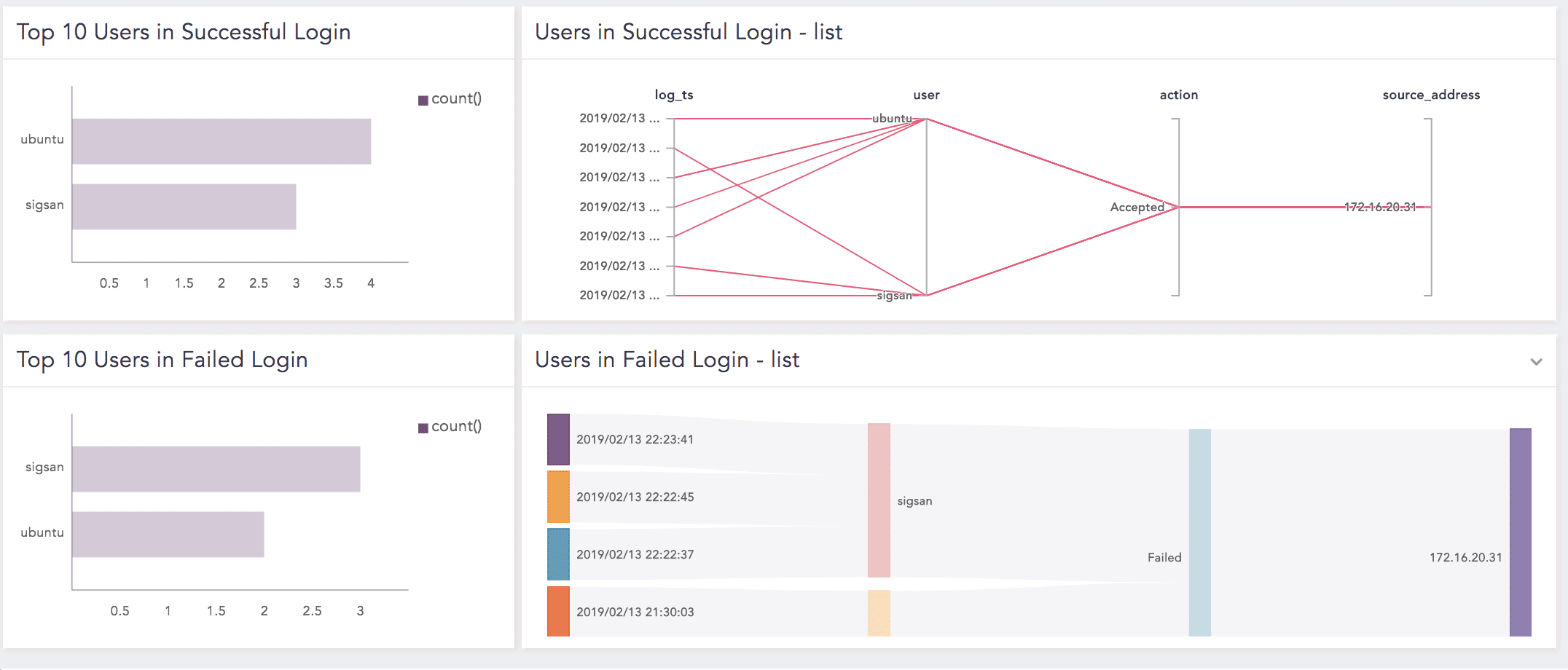
Cron, Job |
Events with the pam_unix(cron:session) message. |
Cron, Job |
Events with the /USR/SBIN/CRON message. |
Cron, Job |
Events with the CRON or cron process. |
NSCD |
Events with the nscd process. |
Successful |
Events with the Successful, Success, or Login successful status. |
Fail |
Events with the Failed, Fail, or Login failed status. |
Login |
Events with the object in authentication, keyboardinteractive/pam, publickey, or password. |
User, Login, Successful |
Events with the Accepted Password, Accepted publickey, or Session opened. |
User, Login, Fail |
Events with the Authentication Failure or Failed Password. |
User, Logoff |
Events with the Session closed message. |
User, Account, Management, Password, Change |
Events with the Password changed message. |
User, Account, Management, Remove |
Events with the Delete user message. |
User, Account, Management, Create |
Events with the A new user message. |
Privilege, Access |
Events with the sudo or su process. |
Service, Start |
Events with the Starting or Start action for all Unix services. |
Service, Restart |
Events with the Re-starting, Restarting, or Restart action for all Unix services. |
Service, Stop |
Events with the Stop or Stopping action for all Unix services. |
FTP |
Events with the ftp or ftpd process. |
ssh |
Events with the sshd process. |
Command, Execute |
Events with the Unix command. |
Remove |
Events with the Delete or Deleted action. |
Modify |
Events with the Replace action. |
Start, Change, Edit |
Events with the Beign Edit action. |
Add |
Events with the Account added action. |
Remove |
Events with the Account removed action. |