To retrieve the data for a single incident.
GET
https://Logpoint-IP/get_data_from_incident
Parameter |
Value Type |
Description |
|---|---|---|
username |
String |
A Logpoint username |
secret_key |
String |
Secret key of Logpoint. Refer to Finding the Access Key. |
requestData |
JSON Object |
A JSON objects containing the following parameters: incident_obj_id: Value of the object ID of the particular incident. incident_id: Value of the field ‘incident_id’ of the particular incident. |
The parameters should be included in the request body as raw text.
{
"username": "John",
"secret_key": "a1b2c3d4e5f6g7h8i9j0k1",
"requestData": {
"incident_obj_id": "6156e859b92e73ec9b0b9bfa",
"incident_id": "a84eba14a93482092a1db865c87516af"
}
}
Note
Content-Type, Content-Length, and Host must be passed in the request header. Content-Type should be application/json.
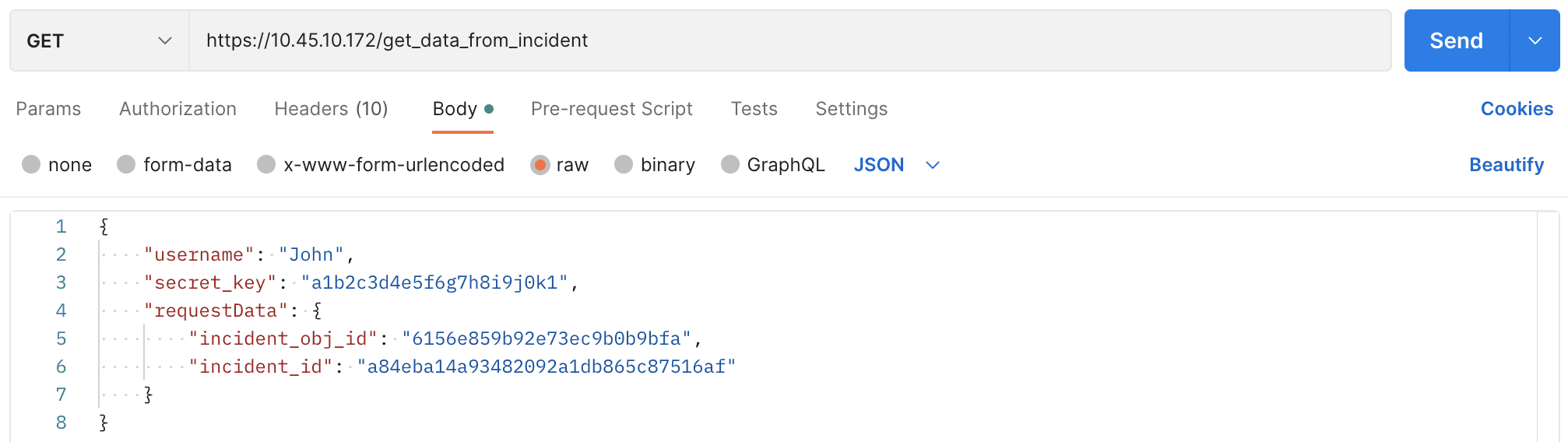
Single Incident Request using Postman.¶
curl --location --request GET 'https://10.45.10.172/get_data_from_incident' \
--header 'Content-Type: application/json' \
--data '{
"username": "John",
"secret_key": "a1b2c3d4e5f6g7h8i9j0k1",
"requestData": {
"incident_obj_id": "6156e859b92e73ec9b0b9bfa",
"incident_id": "a84eba14a93482092a1db865c87516af"
}
}'
{
"success": True,
"rows": [row1, row2, …, rowN]
}
{
"msg": "2021-10-01 10:49:56 Logpoint INFO: dashboard; initialized; type=audit_log; user='admin'; source_address='10.94.128.85'",
"type": "audit_log",
"log_ts": 1633085396,
"_type_str": "msg col_type device_name collected_at device_ip source_name _tz _enrich_policy label norm_id user source_address action host log_level object type _fromV550 repo_name Logpoint_name",
"device_name": "localhost",
"_offset": 247101,
"Logpoint_name": "Logpoint",
"source_address": "10.94.128.85",
"host": "Logpoint",
"action": "initialized",
"repo_name": "_Logpoint",
"source_name": "/opt/immune/var/log/audit/webserver.log",
"col_ts": 1633085404,
"_tz": "UTC",
"log_level": "INFO",
"norm_id": "Logpoint",
"_identifier": "0",
"collected_at": "Logpoint",
"device_ip": "127.0.0.1",
"_fromV550": "t",
"_enrich_policy": "None",
"_type_num": "log_ts col_ts sig_id _offset _identifier",
"_type_ip": "device_ip source_address",
"sig_id": "644573",
"col_type": "filesystem",
"user": "admin",
"object": "dashboard",
"_labels": [
"Audit",
"Logpoint",
"KB",
"Dashboard"
]
},
{
"terminal_type": "unknown",
"msg": "Oct 1 10:49:41 Logpoint sudo: loginspect : TTY=unknown ; PWD=/opt/makalu/installed/webserver ; USER=root ; COMMAND=/opt/immune/installed/system/root_actions/fwrunner.py -l warning -c /opt/immune/etc/config/0_boot_firewall/config.yaml",
"log_ts": 1633085394,
"caller_user": "loginspect",
"path": "/opt/makalu/installed/webserver",
"_type_str": "msg col_type device_name collected_at device_ip source_name _tz _enrich_policy label norm_id caller_user command host path process terminal_type user _fromV550 repo_name Logpoint_name",
"device_name": "localhost",
"_offset": 193798,
"Logpoint_name": "Logpoint",
"host": "Logpoint",
"repo_name": "_Logpoint",
"source_name": "/var/log/auth.log",
"col_ts": 1633085394,
"process": "sudo",
"_tz": "UTC",
"norm_id": "Logpoint",
"command": "/opt/immune/installed/system/root_actions/fwrunner.py -l warning -c /opt/immune/etc/config/0_boot_firewall/config.yaml",
"_identifier": "0",
"collected_at": "Logpoint",
"device_ip": "127.0.0.1",
"_fromV550": "t",
"_enrich_policy": "None",
"_type_num": "col_ts log_ts sig_id _offset _identifier",
"_type_ip": "device_ip",
"sig_id": "10540",
"col_type": "filesystem",
"user": "root",
"_labels": [
"Issue",
"Execute",
"Command",
"Logpoint"
]
}
We are glad this guide helped.
Please don't include any personal information in your comment
Contact Support