Log sources for Palo Alto Network Firewall can be configured using Log Source Template or Devices. Log Source Template is recommended to minimize setup requirements and eliminate normalization issues.
You must create a log source using the log source template to receive the normalized Palo Alto Network Firewall logs. Go to Creating Log Source via a Template to learn more.
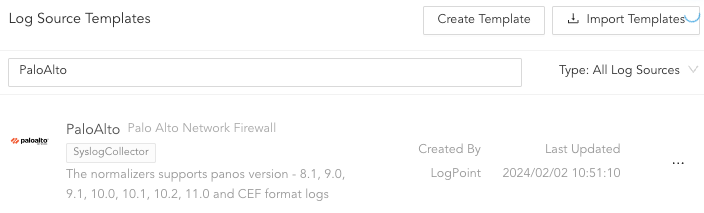
Selecting PaloAlto Log Source Template¶
Go to Settings >> Configuration from the navigation bar and click Repos.
Click Add.
Enter a Repo Name.
Select a Repo Path to store incoming logs.
Set a Retention Day to keep logs in a repository before they are automatically deleted.
Note
You can add and remove multiple Repo Path and Retention Day.
Select a Remote LogPoint and set a Available for (day).
Click Submit.
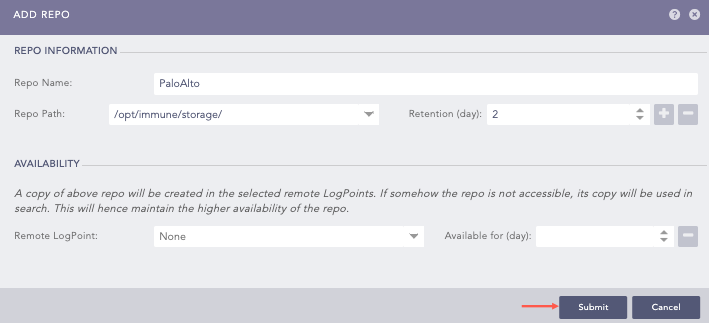
Adding a Repo¶
Go to Settings >> Configuration from the navigation bar and click Normalization Policies.
Click Add.
Enter a Policy Name.
Select the Compiled Normalizer and Normalization Packages for Palo Alto Network Firewall.
Click Submit.

Adding a Normalization Policy¶
Go to Settings >> Configuration from the navigation bar and click Processing Policies.
Click Add .
Enter a Policy Name.
Select the previously created Normalization Policy.
Select the Enrichment Policy.
Select the Routing Policy.
Click Submit.
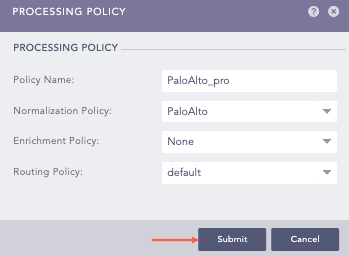
Adding a Processing Policy¶
Go to Settings >> Configuration from the navigation bar and click Devices.
Click Add.
Enter a device Name.
Enter the Palo Alto Network Firewall server IP address(es).
Select the Device Groups.
Select an appropriate Log Collection Policy for the logs.
Select a collector or a forwarder from the Distributed Collector drop-down.
Note
It is optional to select the Device Groups, the Log Collection Policy and the Distributed Collector.
Select a Time Zone. The timezone of the device must be same as its log source.
Configure the Risk Values for Confidentiality, Integrity and Availability used to calculate the risk levels of the alerts generated from the device.
Click Submit.
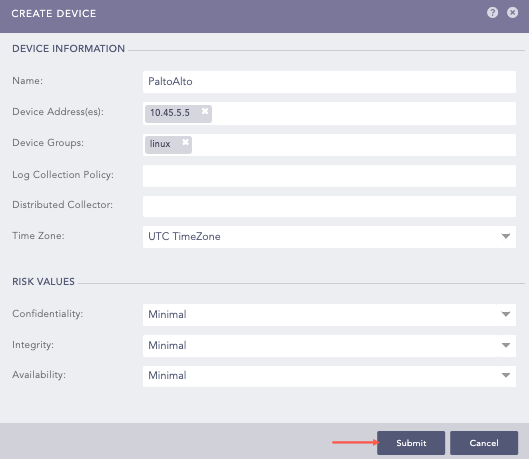
Creating Palo Alto Network Firewall as a device¶
Go to Settings >> Configuration from the navigation bar and click Devices.
Click the Add icon from Actions of the previously added device.
Click Syslog Collector.
Note
You can select a different collector depending on your requirements and added device. To learn more about available collectors go to collectors. If you require assistance, contact our support team.
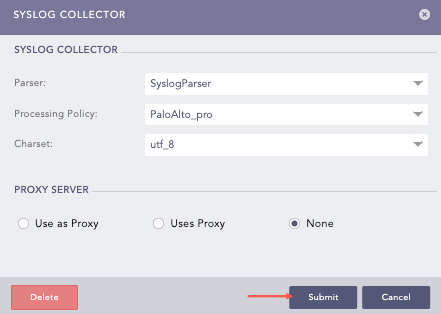
Select Syslog Parser as Parser.
Select the previously created Processing Policy.
Select the Charset.
In Proxy Server, select None
Click Submit.
Available Collectors Fetchers¶
We are glad this guide helped.
Please don't include any personal information in your comment
Contact Support