You can also use the ADFS authentication in Director Console. ADFS (Active Directory Federation Services) allows single sign-on (SSO) authentication for Director Console based on your local Active Directory login.
Note
You must have a unique email address attributed to your ADFS account to use the ADFS service. The SAM Account Name must also be unique for each user.
When you change the role of any user in the LDAP or ADFS authentication from the respective directory server, the new role only enters into effect from the next login.
Log in as the root user.
Go to Authentication >> ADFS.
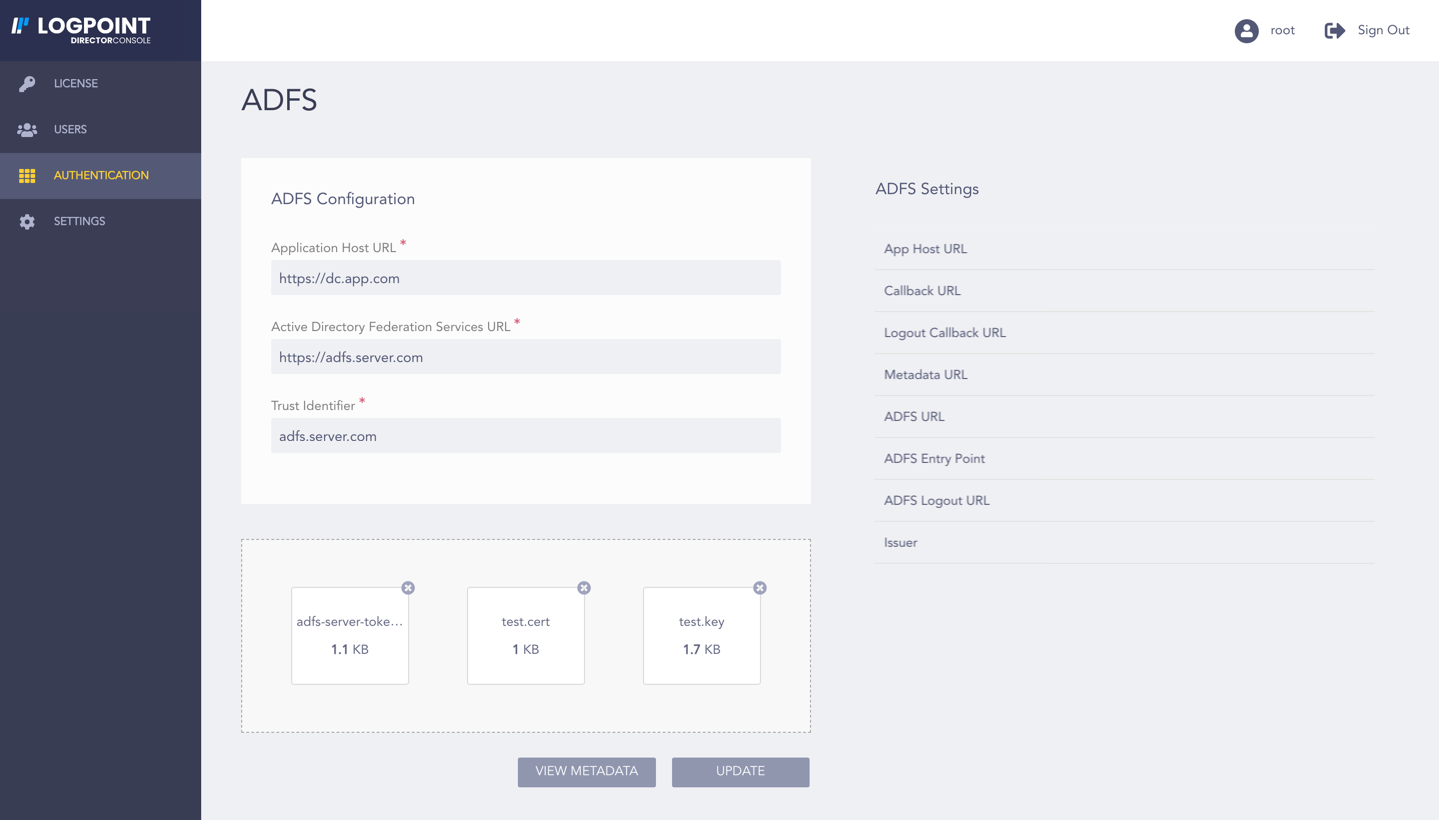
ADFS Configuration¶
In the ADFS Configuration section, enter the Application Host URL, the Active Directory Federation Services URL, and the Trust Identifier.
Note
We recommend you use the name of the server that is used to generate the token-signing certificate, as the name of the Trust Identifier. It is a unique identifier for the Relying Party Trust added to the ADFS server.
Upload the Certificate pair and the ADFS token-signing certificate.
Note
You can obtain the ADFS token signing certificate from the AD FS Server. The ADFS token-signing certificate must have a .cer extension.
Refer to the Generating AD FS Certificate section for details.
Click Update to save the settings.
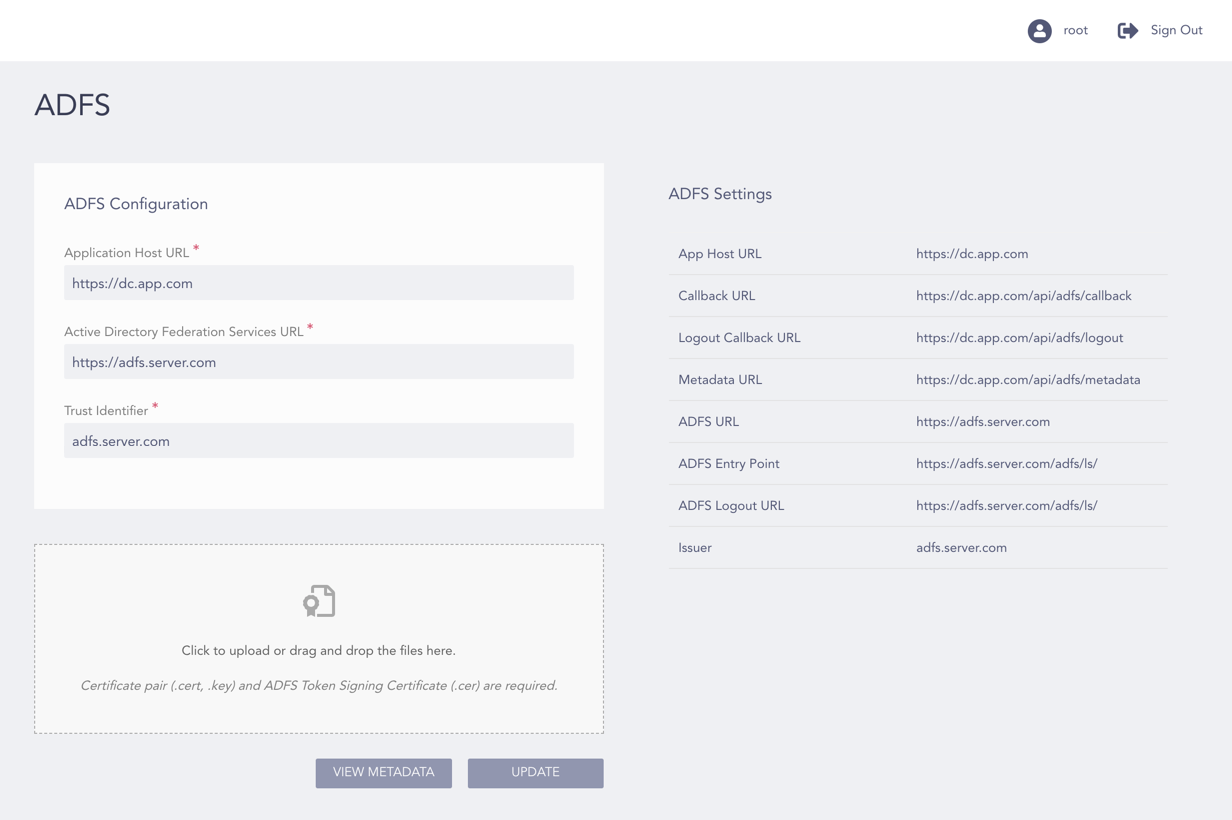
Updated ADFS Configuration Page¶
Click View Metadata to view the metadata used to configure Relying Party Trusts.
Open Server Manager in your Windows machine.
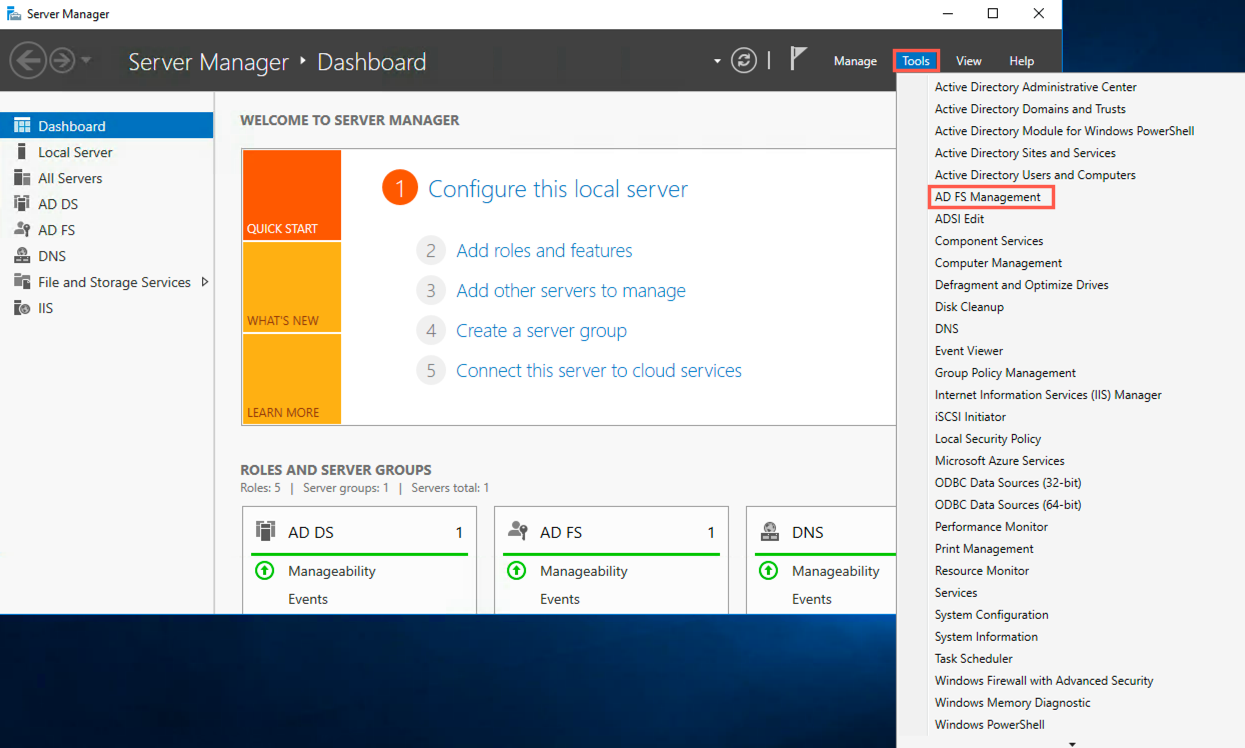
Server Manager¶
Click Tools and select AD FS Management. It opens up the AD FS management console.

AD FS Management Console¶
Expand Service and select Certificates.
Select the Token-Signing certificate from the list of certificates.

Token Signing Certificate¶
Go to the Details section of the Certificates tab.
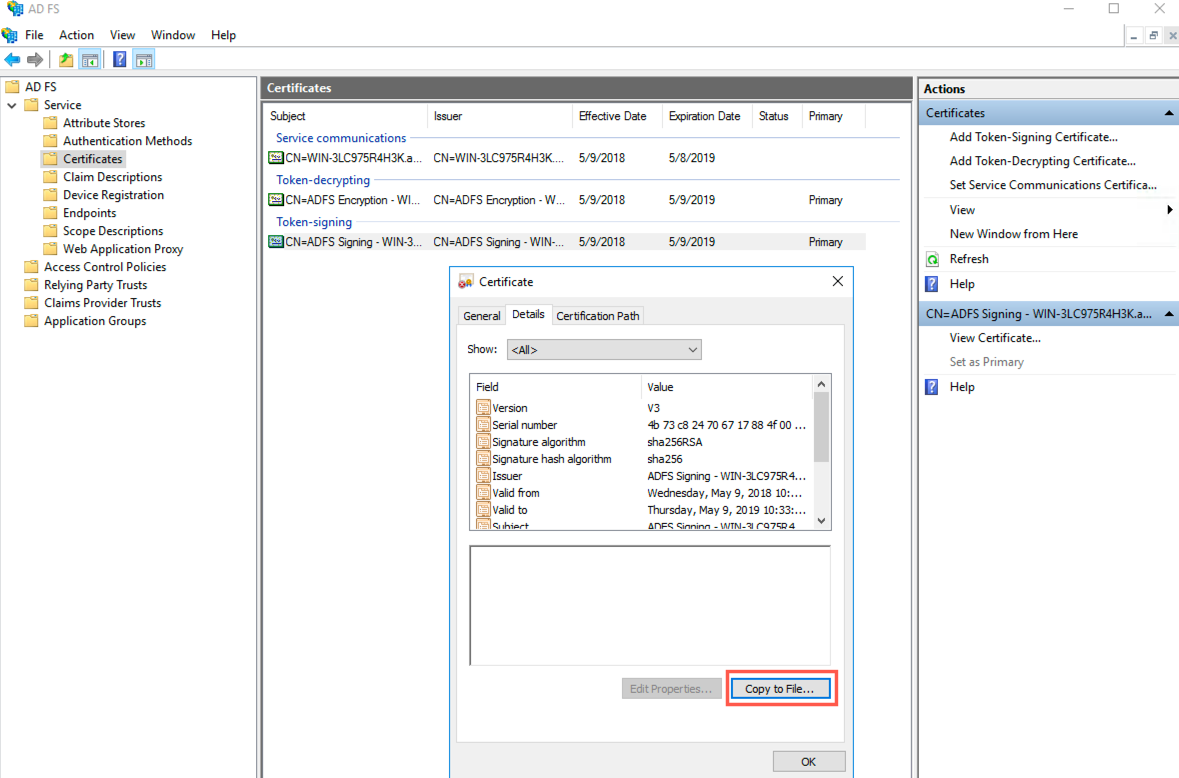
Certificate Wizard¶
Click Copy to File. It opens up the Certificate Export Wizard.

Certificate Export Wizard¶
Click Next.
Select the Base-64 encoded X.509 (.CER) format.

Certificate Export Wizard¶
Click Next.
Enter a File name and click Next.
Click Browse to select a location to save the file.

Saving the File¶
Click Finish to complete the export.
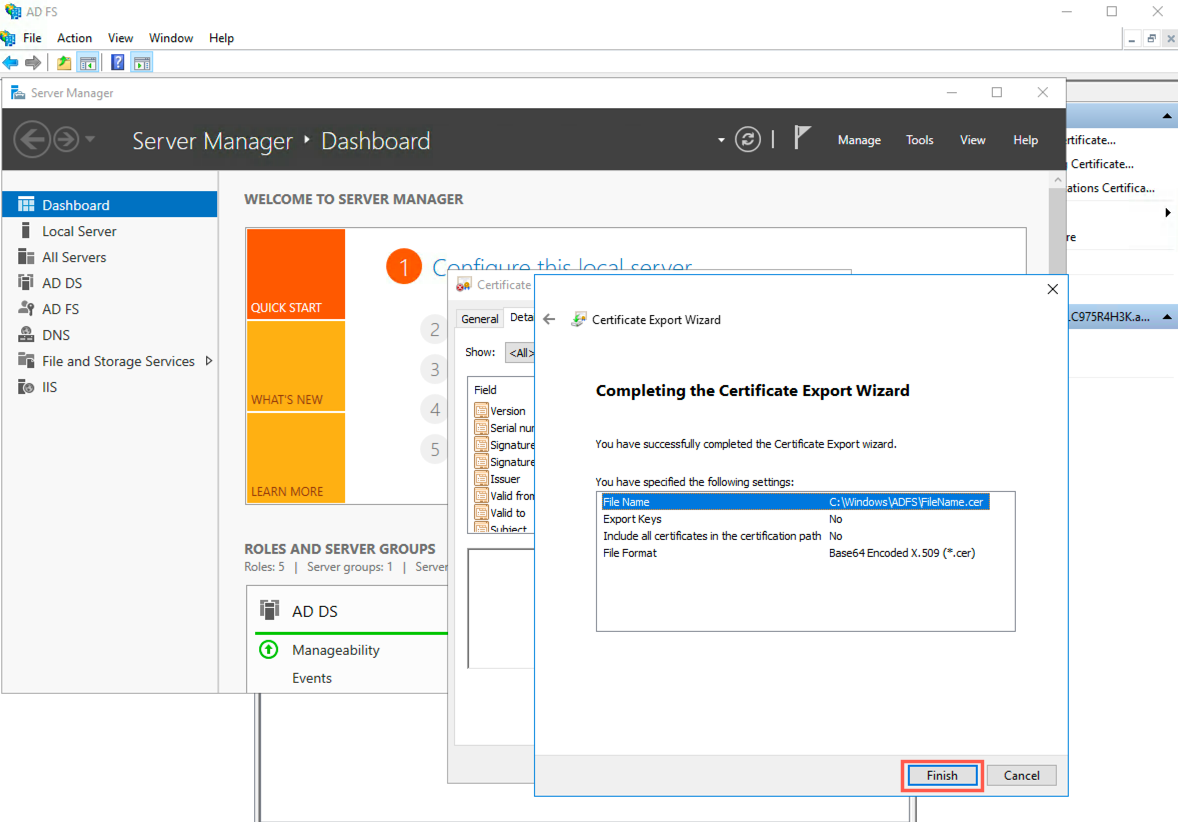
Finishing the Export¶
Open the AD FS Management console.
In AD FS >> Relying Party Trusts, right click and select Add Relying Party Trust.
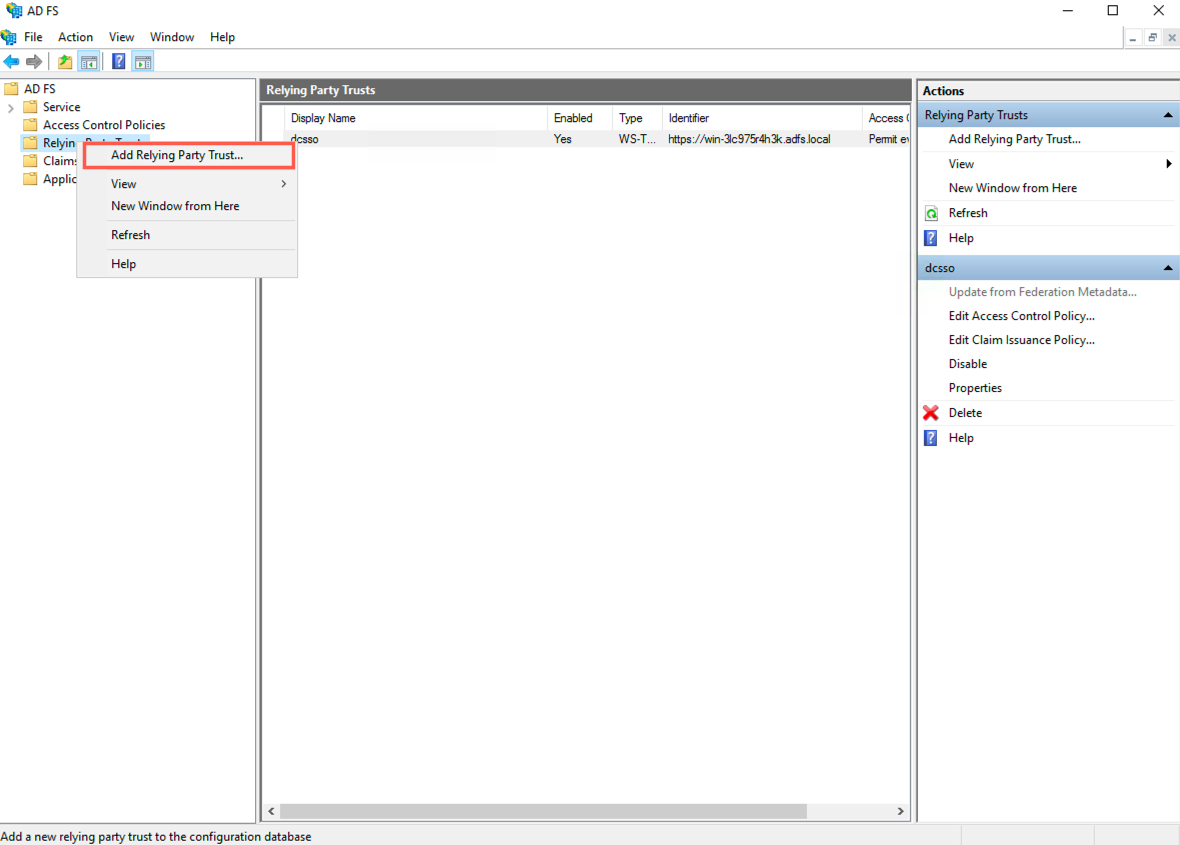
Adding Relying Party Trusts¶
Click Start on the welcome page of the Add Relying Party Trust Wizard.

Click Start¶
On the Select Data Source page, select the Import data about the relying party from a file option.

Selecting the Data Source¶
Import the previously created XML file and click Next.
Enter the Display Name for the application on the Specify Display Name page.
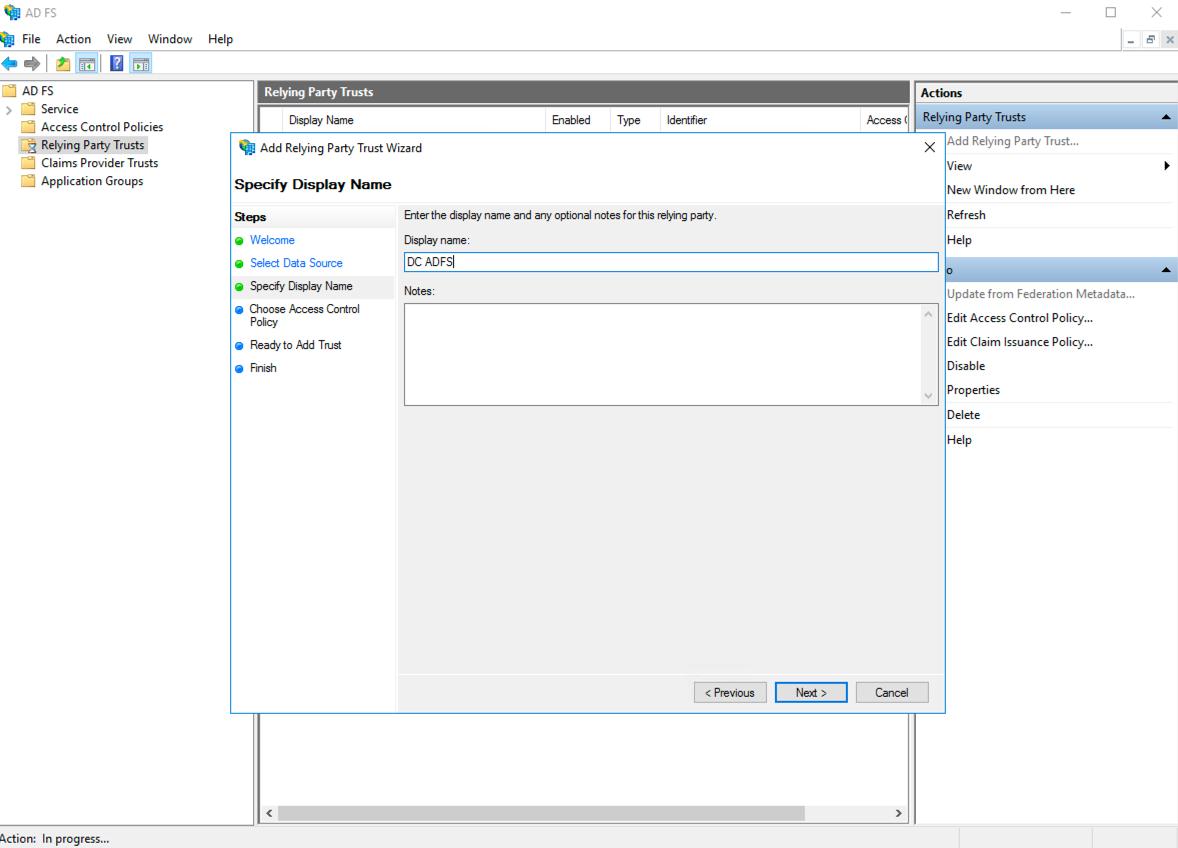
Display Name¶
Click Next.
Select an access control policy under Choose an access control policy.

Choosing an Access Control Policy¶
Click Next. This action takes you to the Ready to Add Trust page.
Click Next on the Ready to Add Trust page.
Select the Configure claims insurance policy for this application option on the Finish page.
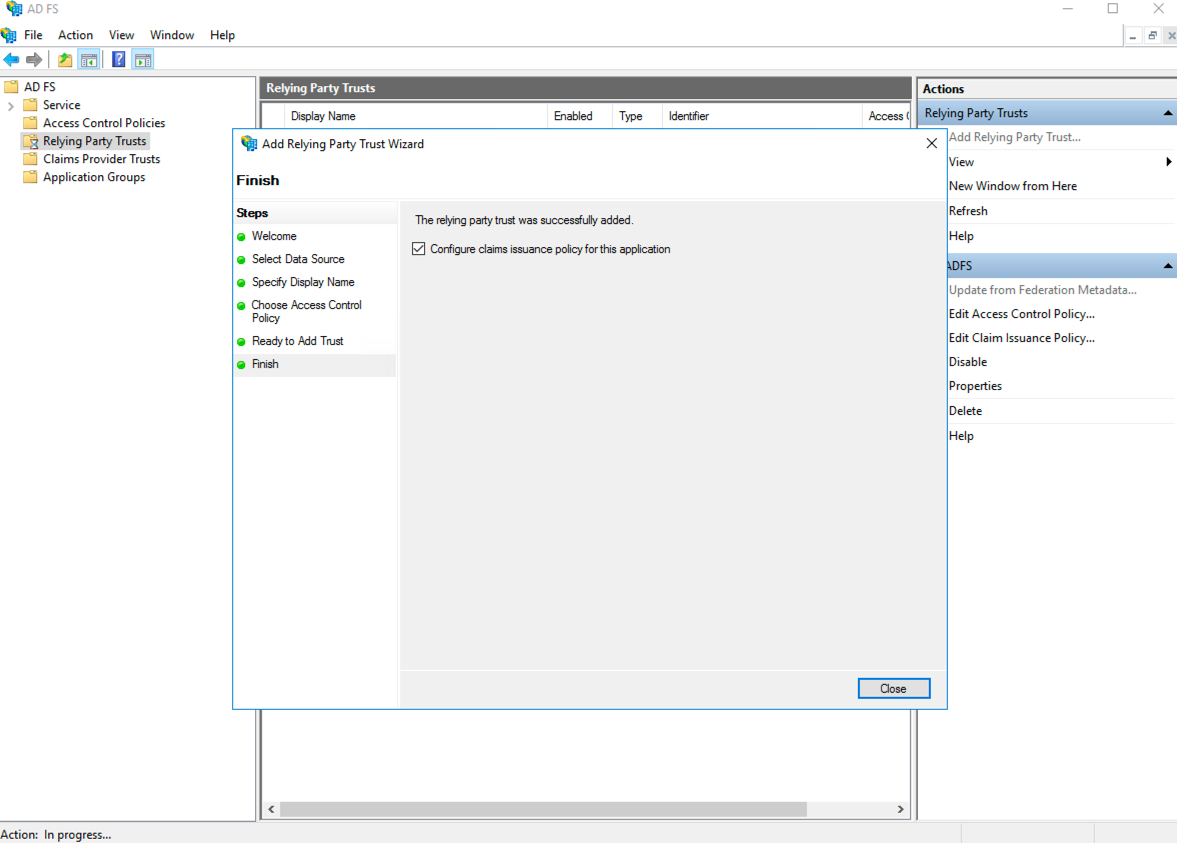
Finishing the Process¶
Click Close.
After you have successfully added a Relying Party Trust, click the Edit Claim Issuance Policy option. It opens up the Edit Claim Issuance Policy for Application tab.

Editing Claim Issuance Policy¶
Click Add Rule. It opens up the Add Transform Claim Rule Wizard.
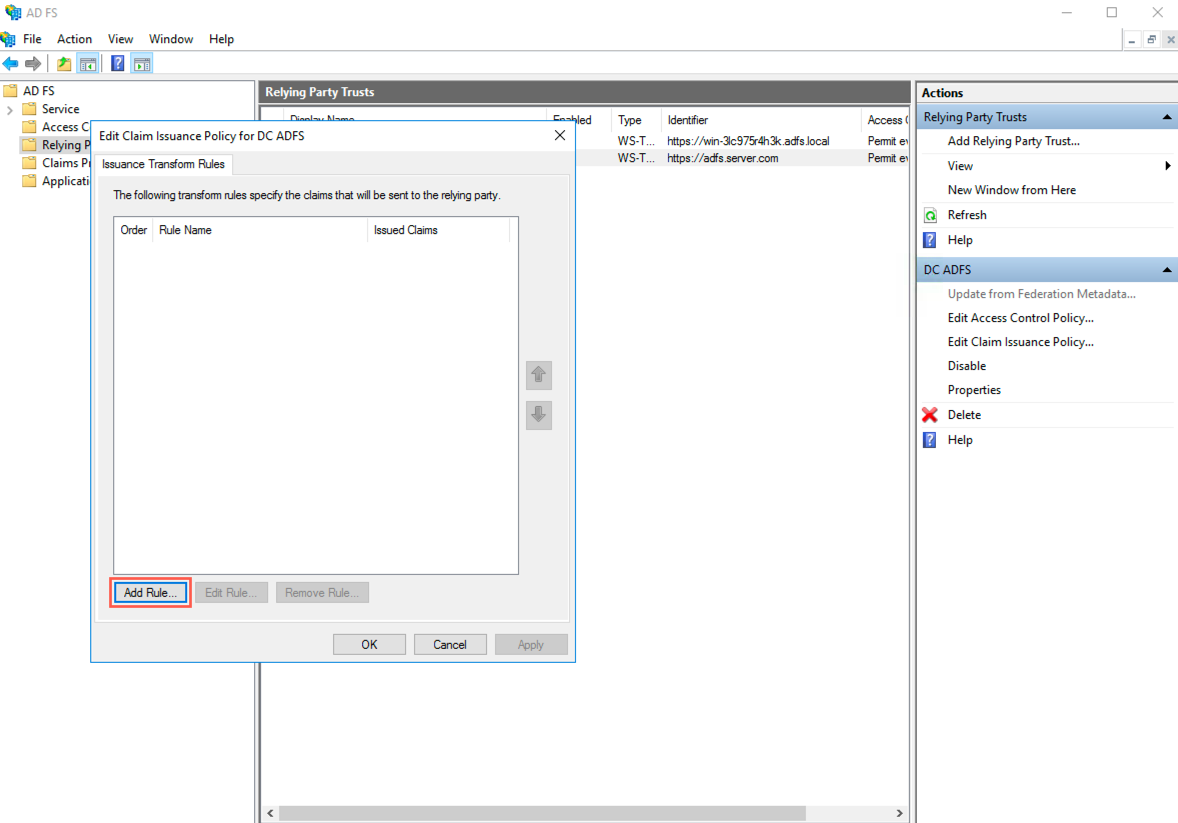
Adding a New Rule¶
Click Next.

Selecting a Rule Template¶
In the Configure Rule page:
4.1. Enter a Claim rule name.
4.2. Select Active Directory as the Attribute store.
4.3. In the Mapping of LDAP attributes to outgoing claim types table, map the following:
4.3.1. Select User-Principal-Name as an LDAP Attribute and UPN as an Outgoing Claim Type.
4.3.2. Select User-Principal-Name as an LDAP Attribute and UID as an Outgoing Claim Type.
4.3.3. Select Is-Member-Of-DL as an LDAP Attribute and Group as an Outgoing Claim Type.
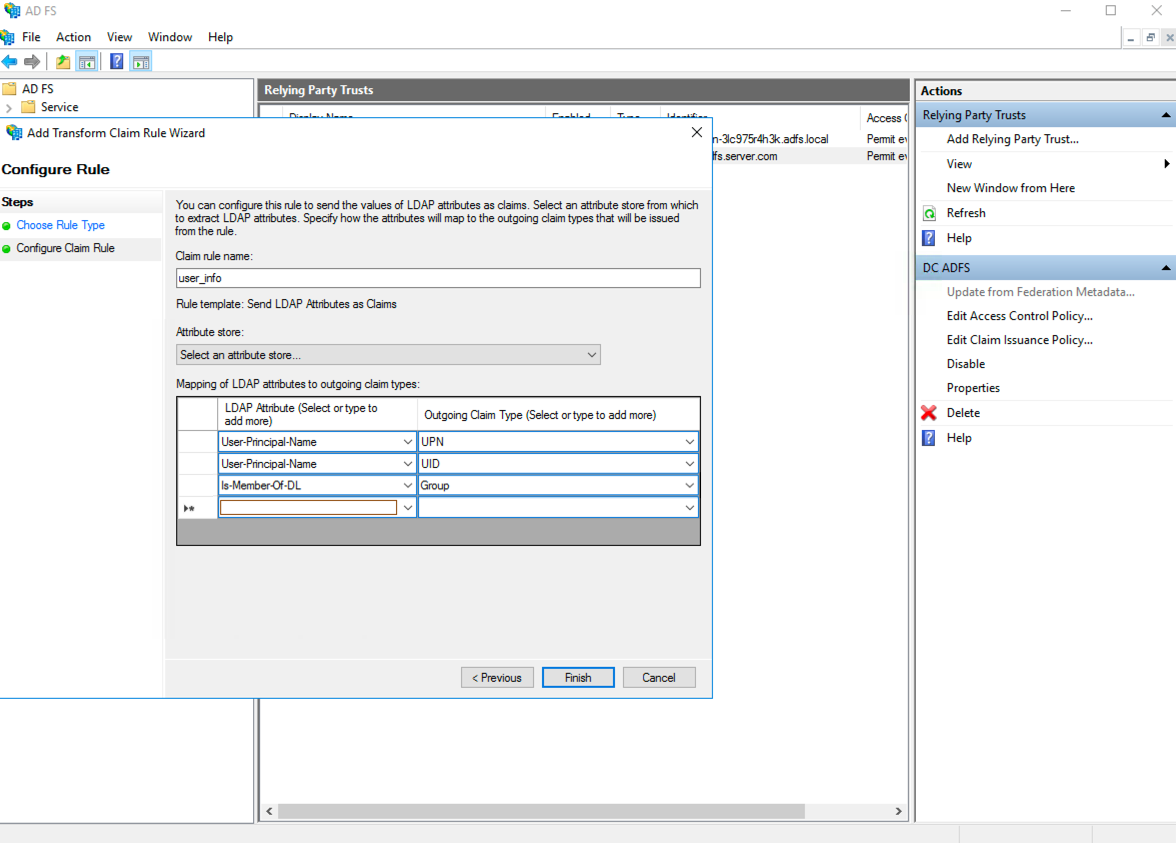
Configuring Claim Rule¶
Click Finish. This action redirects you to the Edit Claim Issuance Policy for Application tab.
Click Add Rule. It opens up the Add Transform Claim Rule Wizard.
Click Next with the default Claim rule template.
In the Configure Rule page:
8.1. Enter a Claim rule name.
8.2. Select Active Directory as the Attribute Store.
8.3. In the Mapping of LDAP attributes to outgoing claim types table, select E-Mail-Addresses as an LDAP Attribute and E-Mail Address as an Outing Claim Type.

Configuring Claim Rule¶
Click Finish. This action redirects you to the Edit Claim Issuance Policy for Application tab once again.
Click Add Rule. It opens up the Add Transform Claim Rule Wizard. Select Transform an Incoming Claim as the Claim rule template.

Selecting a Rule Template¶
Click Next.
In the Configure Rule page:
12.1. Enter a Claim rule name.
12.2. Select E-Mail Address as the Incoming claim type.
12.3. Select Name ID as the Outing claim type.
12.4. Select Email as the Outgoing name ID format.
12.5. Select Pass through all claim values.

Configuring Claim Rules¶
Click Apply.

Edit Claim Issuance Policy for adfs-dc Tab¶
We are glad this guide helped.
Please don't include any personal information in your comment
Contact Support