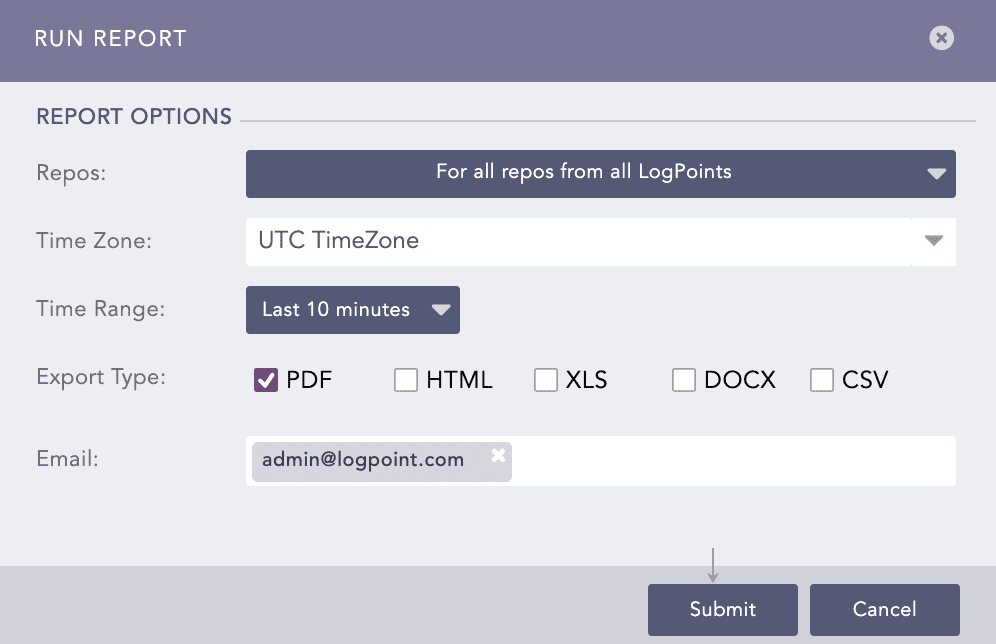
Update, Successful |
Trend Micro events with the UPDATE_SUCCESS event category. |
Product, Service, Start |
Trend Micro events with the PRODUCT_SERVICE_STARTED event category. |
Product, Service, Stop |
Trend Micro events with the PRODUCT_SERVICE_STOPPED event category. |
Update, Fail |
Trend Micro events with the UPDATE_FAIL event category. |
Unknown |
Trend Micro events with the UNKNOWN event category. |
Spyware, Malware |
Trend Micro events with the GRAYWARE event category. |
Virus, Malware |
Trend Micro events with the VIRUS event category. |
Quarantine |
Trend Micro events with the QUARANTINE event category. |
Clean |
Trend Micro events with the CLEAN event category. |
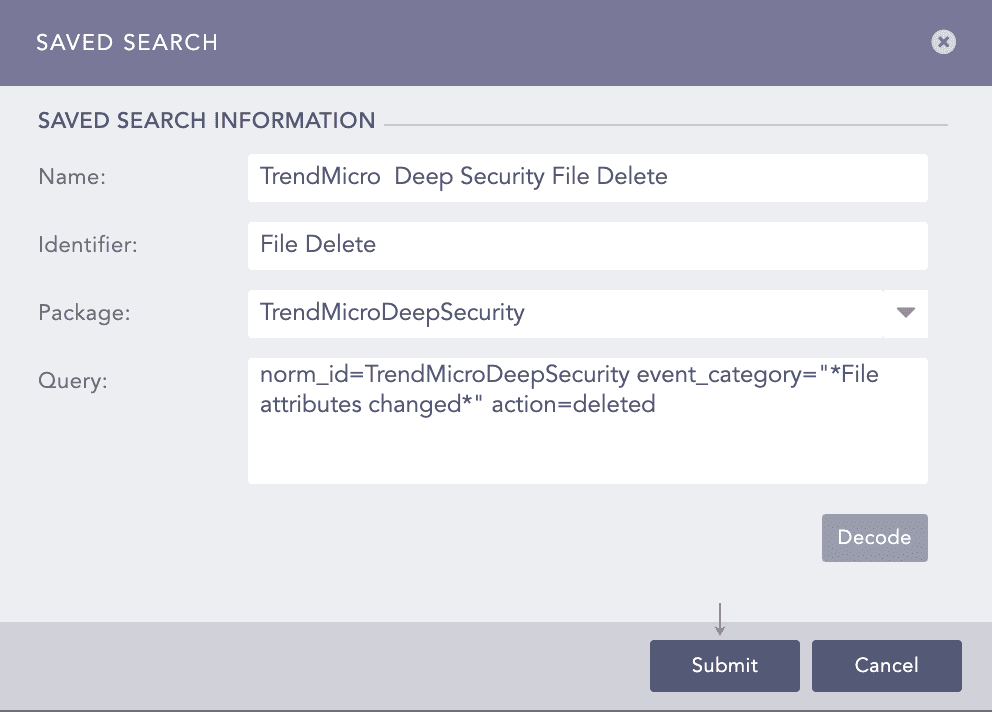
Delete |
Trend Micro events with the DELETE event category. |
Successful |
Trend Micro events with the SUCCESS event category. |
Malware |
Trend Micro events with the MALWARE event category. |
Remove, Fail |
Trend Micro events with the PASS_THRU event category. |
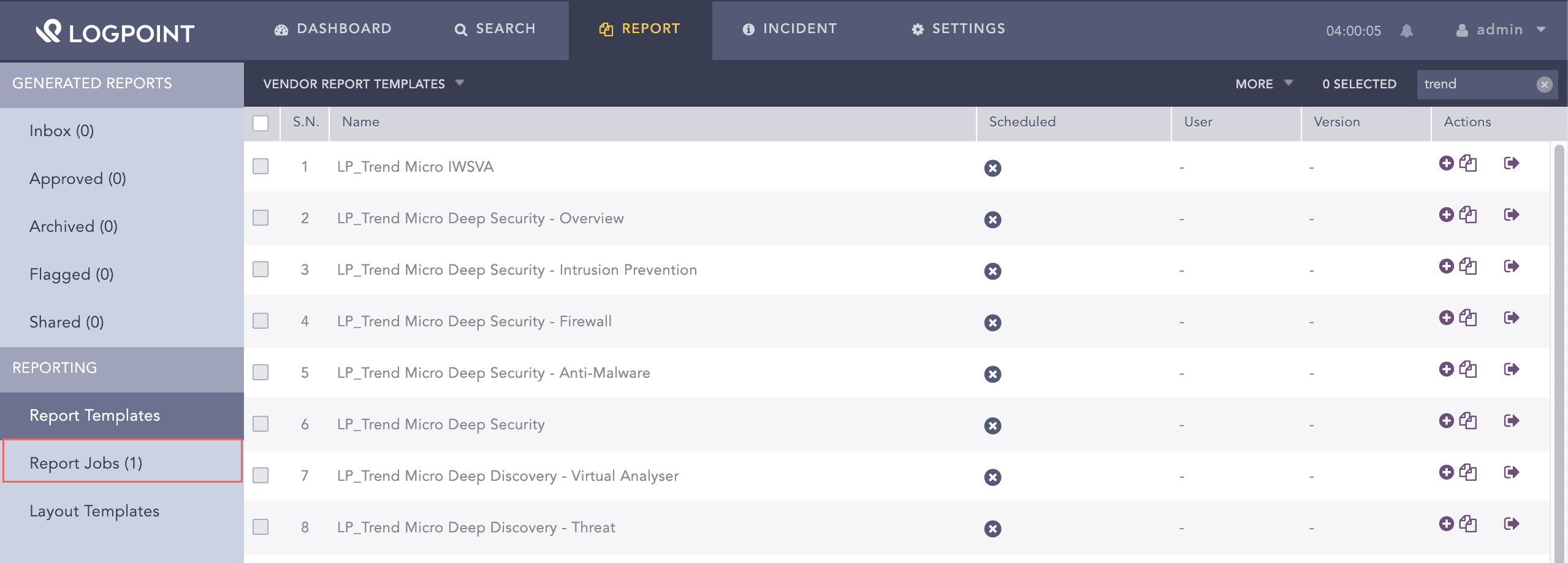
Firewall |
Trend Micro Deep Security event with the event ID 20. |
Intrusion, Prevention |
Trend Micro Deep Security event with the event ID 10. |
Firewall, Rule, Deny |
Trend Micro Deep Security event with the event ID 21. |
Integrity, Monitor, Rule |
Trend Micro Deep Security event with the event ID 30. |
Log, Inspect, Rule |
Trend Micro Deep Security event with the event ID 40. |
Intrusion, Prevention, Internal, Error |
Trend Micro Deep Security event with the event ID 2. |
Intrusion, Prevention, Normalization |
Trend Micro Deep Security event with the event IDs 5,6,7, or 8. |
Intrusion, Prevention, Rule |
Trend Micro Deep Security event with the event ID 1. |
Log, Inspect, Rule |
Trend Micro Deep Security event with the event ID 3. |
SSL |
Trend Micro Deep Security event with the event ID 3. |
Firewall |
Trend Micro Deep Security event with the event ID 1. |
Antimalware |
Trend Micro Deep Security event with the event ID 4. |
Web, Reputation |
Trend Micro Deep Security event with the event ID 5. |
Application, Control |
Trend Micro Deep Security event with the event ID 6. |
Antimalware, Realtime, Scan |
Trend Micro Deep Security event with the event ID 4000000. |
Antimalware, Manual, Scan |
Trend Micro Deep Security event with the event ID 4000001. |
Antimalware, Schedule, Scan |
Trend Micro Deep Security event with the event ID 4000002. |
Antimalware, Quick, Scan |
Trend Micro Deep Security event with the event ID 4000003. |
Antispyware, Realtime, Scan |
Trend Micro Deep Security event with the event ID 40000010. |
Antispyware, Manual, Scan |
Trend Micro Deep Security event with the event ID 40000011. |
Antispyware, Schedule, Scan |
Trend Micro Deep Security event with the event ID 40000012. |
Antispyware, Quick, Scan |
Trend Micro Deep Security event with the event ID 40000013. |
Suspicious, Activity, Realtime, Scan |
Trend Micro Deep Security event with the event ID 40000020. |
Unauthorized, Change, Realtime, Scan |
Trend Micro Deep Security event with the event ID 40000030. |
Web, Reputation, Block |
Trend Micro Deep Security event with the event ID 5000000. |
Web, Reputation, Detect |
Trend Micro Deep Security event with the event ID 5000001. |
Application, Control, Detect, Blacklist |
Trend Micro Deep Security event with the event ID 6001100. |
Application, Control, Detect, Absent, Whitelist |
Trend Micro Deep Security event with the event ID 6001200. |
Application, Control, Block, Blacklist |
Trend Micro Deep Security event with the event ID 6002100. |
Application, Control, Block, Absent, Whitelist |
Trend Micro Deep Security event with the event ID 6002200. |
Firewall |
Trend Micro events with the Log for TCP Port event category. |
Intrusion, Prevention |
Trend Micro events with the Intrusion Prevention Rule event category. |
User, Successful, Login |
Trend Micro events with the User Signed In event category. |
Integrity, Monitor |
Trend Micro events with the New Integrity Monitoring Rule event category. |
Web, Reputation |
Trend Micro events with the Web Reputation event category. |
Appliance, Error |
Trend Micro events with the Agent or Appliance Error event category. |
Directory, Synchronize, Complete |
Trend Micro events with the User Synchronization Finished event category. |
Send, Report |
Trend Micro events with the Sending Report event category. |
Event, Retrieve |
Trend Micro events with the Events Retrieved event category. |
Alert, Email, Send |
Trend Micro events with the Alert Emails Sent event category. |
Agent, Offline |
Trend Micro events with the Offline event category. |
Internal, Error |
Trend Micro events with the Internal Software Error event category. |
Certificate, Accept |
Trend Micro events with the Certificate Accepted event category. |
Session, Authentication, Fail |
Trend Micro events with the User Session Validation Failed event category. |
Relay, Update, Successful |
Trend Micro events with the Relay Group Update Success event category. |
Relay, Update, Request |
Trend Micro events with the Relay Group Update Requested event category. |
Check, Status, Fail |
Trend Micro events with the Check Status Failed event category. |
Server, Prepare |
Trend Micro events with the Server Prepared event category. |
Synchronize, Complete |
Trend Micro events with the Synchronization Finished event category. |
Synchronization, Request |
Trend Micro events with the Synchronization Requested event category. |
User, Authentication, Fail |
Trend Micro events with the Authentication Failed event category. |
Interface, Synchronize, Fail |
Trend Micro events with the Interfaces Out of Sync event category. |
Virtual, Appliance, Deploy |
Trend Micro events with the Virtual Appliance Deployed event category. |
Interface, Synchronize |
Trend Micro events with the Interfaces in Sync event category. |
Virtual, Machine, Unprotect |
Trend Micro events with the Virtual Machine Unprotected event category. |
Filter, Driver, Upgrade |
Trend Micro events with the Filter Driver Upgraded event category. |
Filter, Driver, Upgrade, Request |
Trend Micro events with the Filter Driver Upgrade Requested event category. |
User, Synchronization, Fail |
Trend Micro events with the User Synchronization Failed event category. |
Alert, Start |
Trend Micro events with the Alert Started event category. |
Antimalware, Engine, Offline |
Trend Micro events with the Antimalware Engine Offline event category. |
Alert, End |
Trend Micro events with the Alert Ended event category. |
SQL, Injection, Prevention |
Trend Micro events with the Generic SQL Injection Prevention event category. |
Out, Allow, Policy |
Trend Micro events with the Out of Allowed Policy event category. |