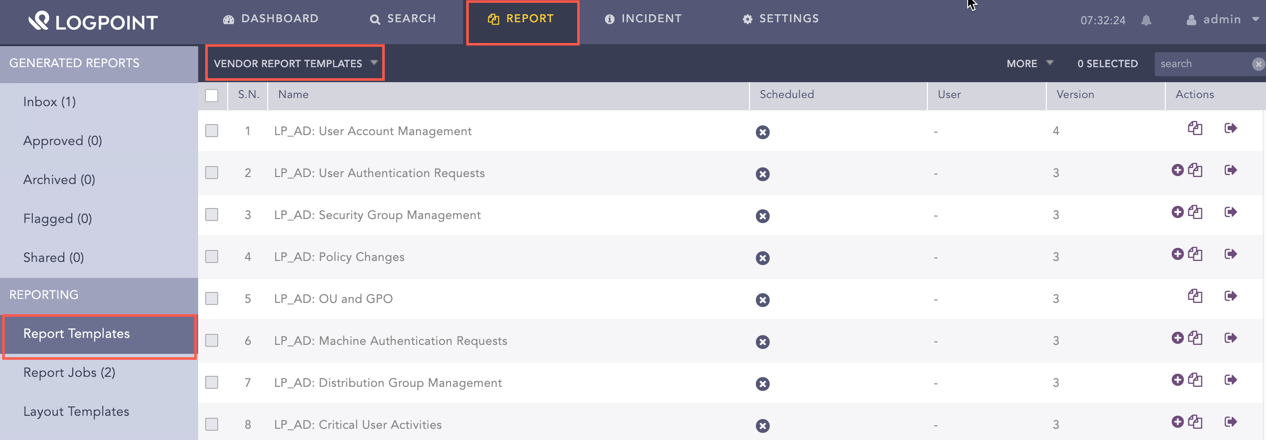
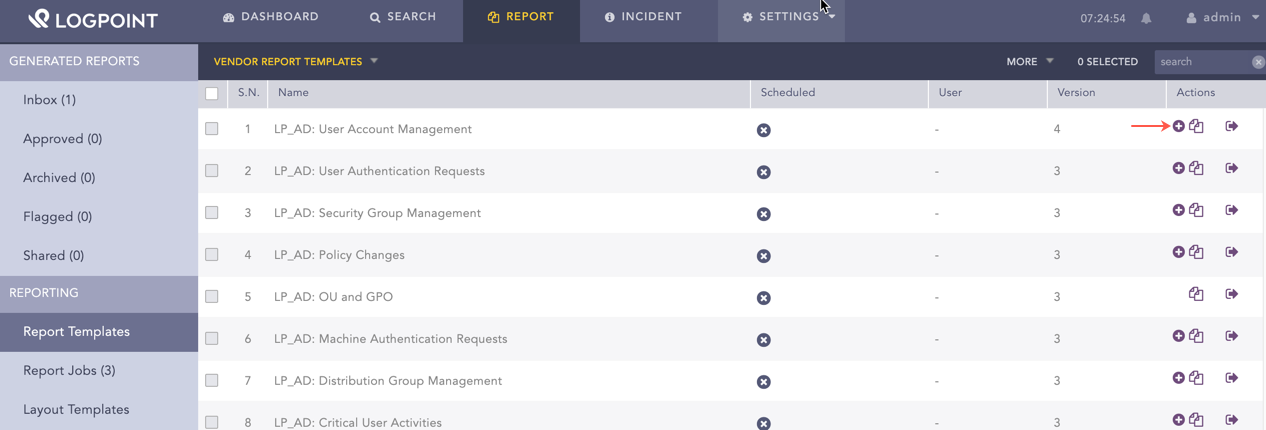
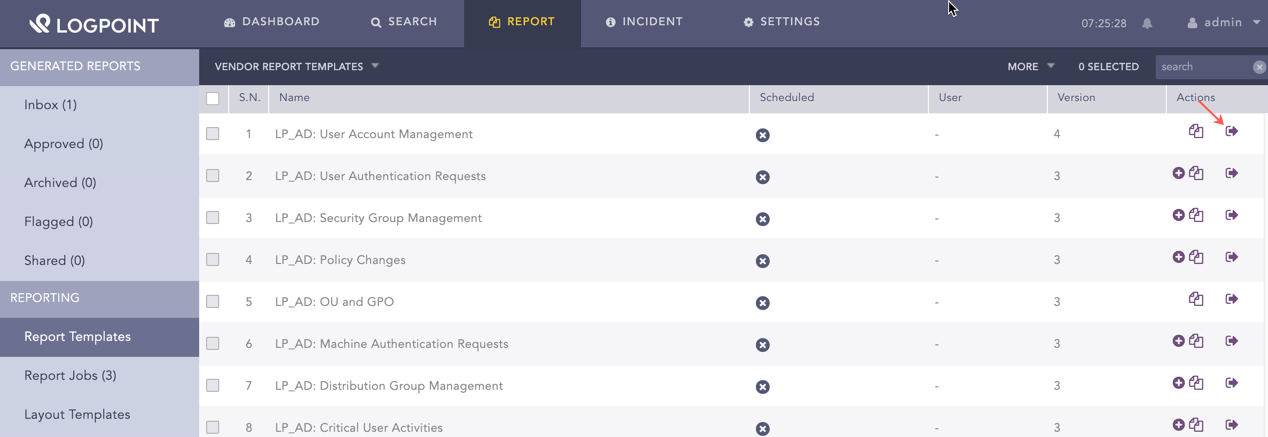
Top 10 Administrative Logins |
The top 10 administrative logins. For this widget to populate, the list ADMINS should be updated. |
Top 10 Successful User Logins |
The top 10 successful user logins when NT authority is passed by server network. |
Successful User Logins - List |
A list of successful user logins. |
Top 10 Failed User Logins |
The top 10 failed user logins when NT authority is denied by server network. |
Failed User Logins - List |
A list of failed user logins based on user, source_address, workstation, action, domain, and reason . |
Top 10 Failed Administrative Logins |
The top 10 failed administrative logins. |
Top 10 Users Logged in from more than 3 Multiple Locations |
The top 10 anonymous users with successful login from more than three devices. |
Top 10 Failed User Logins from Multiple Locations |
The top 10 anonymous users with failed login from multiple locations. |
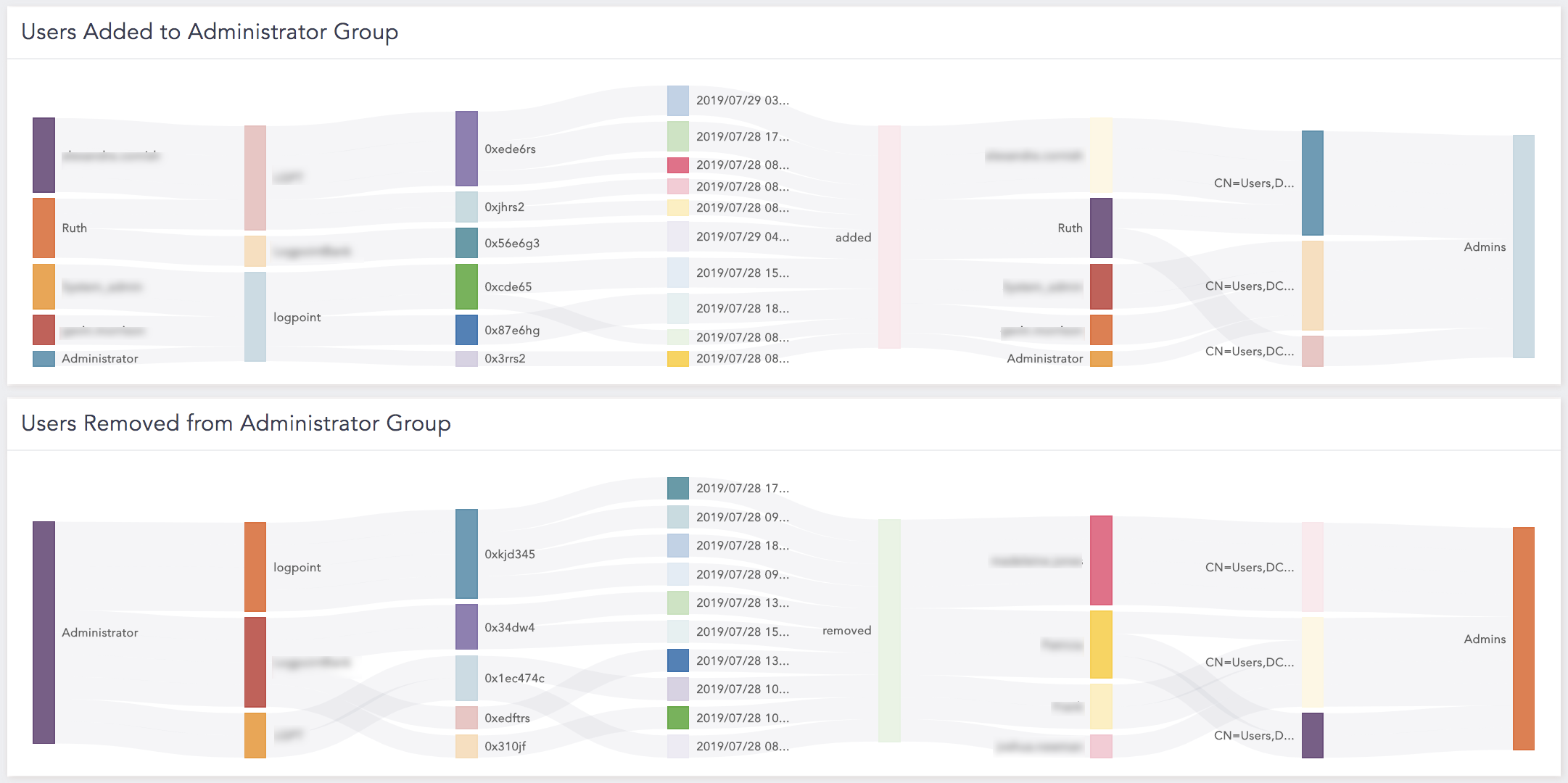
Administrative Logins from Multiple Locations |
Administrative logins from multiple locations to reduce the times that an attacker can compromise the logon session. |
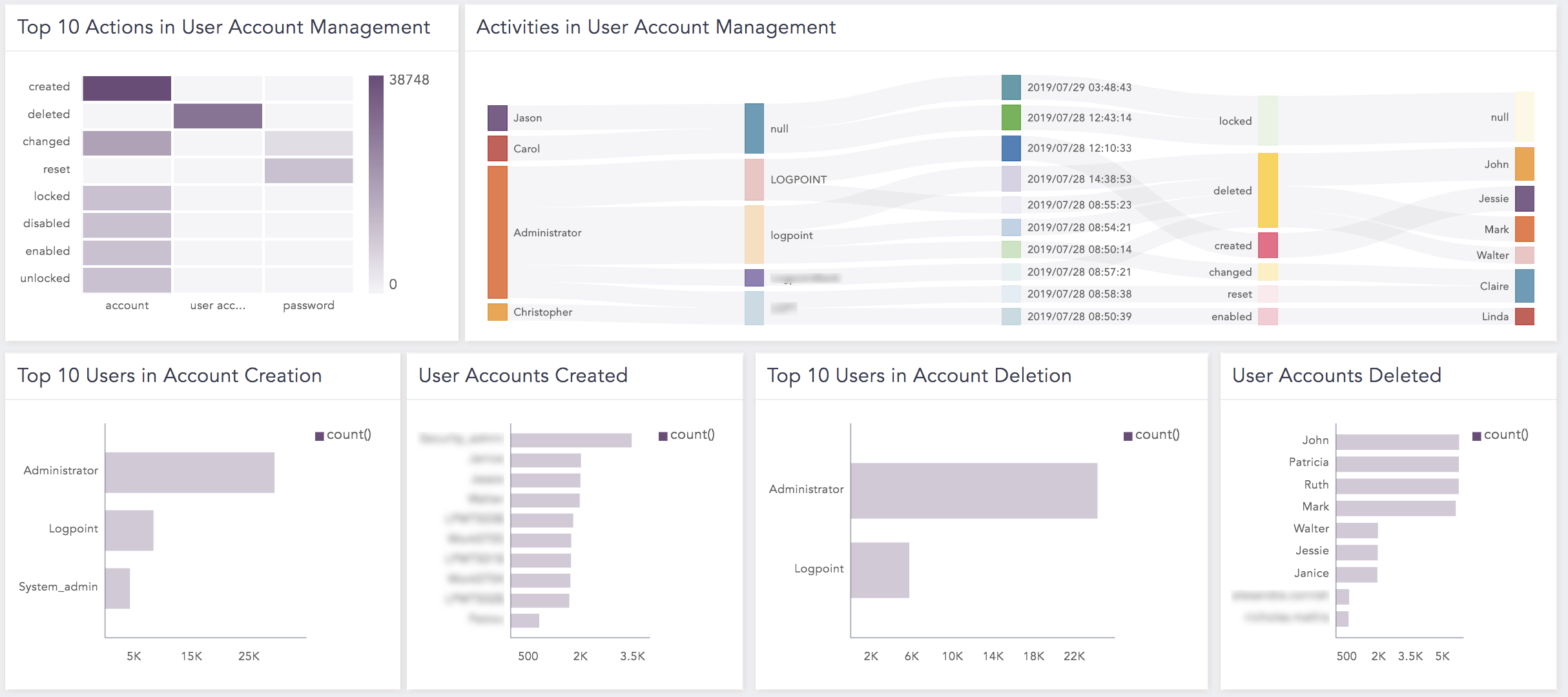
Top 10 User Login Activities |
The top 10 user login activities in user and computer accounts. |
Top 10 Failed Workstation Authentication |
The top 10 failed workstation authentications. |
Remote Interactive Logins - List |
A list of the remote interactive logins based on user, domain, action, source_address, and workstation. |
Failed Administrative Logins from Specific Workstations |
The failed administrative logins from the specific workstations. |
Failure Reasons for Administrative Logins |
Reasons why an administrative login failed, such as a bad password. |
Failed Workstation Authentications |
The failed workstation authentications based on user, source_address, action, object, and reason. |
Reasons or Failure Codes for Failed Workstation Authentication |
Reasons or failure codes, such as 0xC0000064 (Username does not exist) for the failed workstation authentications. |
Failed Authentication Process |
The failed authentication process when users logged with incorrect username and/or password. |
Top 10 Users in Failed Login - User Not Present |
The top 10 users with failed logins due to the unavailability of the user. The sub-status code of this event is 0xc0000064. |
Top 10 Users in Failed Login - Wrong Password |
The top 10 users with failed logins due to wrong passwords. The sub-status code of this event is 0xc000006A. |
Latest User Logins - List |
A list of the latest user logins. |
Users Logged in to Multiple Domains |
A user logged into multiple domains. |
Logon Duration |
The total duration taken by logon to complete for the session. |
Session Disconnected - List |
A list of sessions abruptly disconnected. |
Interactive Login Failure - List |
A list of interactive login failures. |