Authentication and Authorization
Users
There are five types of users in AAHC:
Admin user
Search user
Report user
Report Admin user
Super Admin user
The search users, report users, and super admin users must belong to a user group in the selected IdP, with roles defined by the IdP server and mapped by the admin user in IDP Mapping, for IdP authentication.
Admin User
AAHC’s default admin user is responsible for configuring and managing the following settings:
Search User
A Search user can search the data retrieved from Logpoint and generate reports from them.
The admin user of AAHC assigns one of the following roles to a search user:
User Access: A user with this role can perform the search by User ID.
Patient Access: A user with this role can perform the search by Patient SSN.
All Access: A user with this role can perform the search by both the User ID and Patient SSN parameters.
Besides searching, a search user can also perform the following actions:
Download search results
Download scheduled reports
Generate ad hoc reports
Make actions on a report such as commenting, flagging, reviewing, and archiving
Report User
A Report user can only view the reports generated in AAHC and perform all the report actions except the deletion of reports.
Report Admin User
A Report Admin user can only view the reports generated in AAHC and perform all the report actions including the deletion of reports. They do not have permission to search.
Super Admin User
A Super Admin user can manage other Users, configure Columns and Search Permission Groups, create predefined Search Query and Scheduler for the search users. They can't search or view generated reports. You can assign the Super Admin role to multiple users. To assign roles to users, go to Users.
Log into AAHC
Log in as an Admin User
Enter the AAHC URL in the web browser to open the login page.
Enter admin as the Username and the Password.
The default password for the admin user is set to:
Click Login.
AAHC prompts you to change your password if:
You are logging in for the first time.
You upgrade to AAHC v1.6.0.
AAHC locks users after five unsuccessful login attempts and unlocks them automatically after 15 minutes. However, you can immediately unlock the admin user by executing the unlock-useradmin command in AAHC console.
Logging in via the AAHC Database Authentication (Search / Report / Report Admin / Super Admin)
Users created by the Admin User can log into AAHC via AAHC authentication:
Enter AAHC URL in a web browser to open the login page.
Provide your Username as created by the admin and the Password.
By default, the password is set to:
You can change the password after logging into AAHC.
Click Login.
AAHC prompts you to change your password if:
You are logging in for the first time.
You upgrade to AAHC v1.6.0.
AAHC locks users after five unsuccessful login attempts and unlocks them automatically after 15 minutes. However, to immediately unlock your account, contact your admin user.
Logging in via the Identity Provider (IdP) Authentication
You can log into AAHC via single sign-on (SSO) with your IdP credentials. AAHC collects user information and attribute settings via SAML tokens.
Go to Expected SAML Token Format for AAHC for details on the expected SAML tokens.
You need to configure the IdP settings in AAHC to enable IdP authentication. Go to Authentication Settings to configure the IdP settings.
After configuring the IdP settings, log into AAHC:
Enter AAHC URL in a web browser to open the Login page.
Click IDP Login. It redirects you to the IdP authentication page.
Provide your IdP credentials to access AAHC.
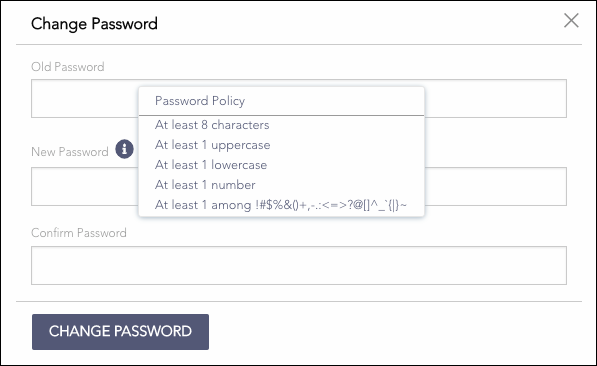
Change Password
Enter the Old Password and the New Password. Make sure to enter a strong password. Click the Information icon for details.
Re-enter the new password to confirm.
Click Change Password.
Expected SAML Token Format for IdP Authentication
AAHC uses SAML tokens to authorize and authenticate Identity Provider (IdP) users. A SAML token should consist of:
A subject with the NameID attribute which has user identifier as the value.
An attribute with the name careProvider and the following two values for this attribute:
HSA id of the care provider as configured in IdP
Display name for the care provider
An attribute with the name careUnitReviewerFor and the following three values for this attribute:
The care provider's HSA-id which is an identifier for each care provider as configured in IdP
Care Unit Reviewer id as configured in IdP
Display name for the care unit reviewer
An attribute with the name Roles and the following value for this attribute:
Role as configured in IdP
The attribute name is case-sensitive.
Example of a SAML token
Last updated
Was this helpful?