Alert Rule API
The Alert Rules API allows you to create, update, list, read, delete, activate, and deactivate alert rules. You must create a token using the following scopes to use the alert rules API.
Scope name
Function
alertrules:write
alertrules:read
Creating an Alert Rule using API
To create alert rules, use AlertRules/create_api.
Endpoint URL
https://Logpoint-IP/AlertRules/create_api
Method
POST
Request Headers
Content-Type:
application/jsonAuthorization:
Bearer <TOKEN>
Parameters
Parameters are data sent with the API request. Include them in the request body as raw JSON.
Field
Type
Description
object
Defines the search query, time range, and repos used to retrieve logs to create an alert rule. Mandatory Field.
object
Additional context for the alert rule, including MITRE ATT&CK tags, log sources, and metadata for categorization. Mandatory Field.
object
Customizes the incidents obtained from the alert rule, including custom Jinja template, or a simple view. Mandatory Field.
name
string
Name of the alert rule. Must be at least 5 characters long. Mandatory Field.
description
string
Information about the alert rule. Optional Field.
Search Parameters
Field
Type
Description
query
string
Query used to search logs. Mandatory Field.
timerange_day, timerange_hour, timerange_minute
integer
Timeframe within which the search is performed. The time range value must be between 1 minute and 30 days. Add at least one field.
repos
string
List of addresses (from the Repos API) to retrieve logs to perform search. Mandatory Field.
limit
integer
Maximum number of logs to retrieve using the query. Default is 100. Optional.
flush_on_trigger
boolean
Ensure the next alert is triggered only based on a new set of events. Default is false. Optional.
search_interval_minute
integer
Search interval in minutes. Must be a factor of the time range value. Default is 10. Optional.
delay_interval_minute
integer
Delay before processing logs to ensure all relevant data is collected (used with log_ts based searches). Default is 0. Optional.
throttling_enabled
boolean
Avoid creating multiple alerts for the same set of values for a specified time. Default is false. Optional.
throttling_field
string
Field name used to apply throttling. Optional.
throttling_time_range
integer
Time range (in minutes) to avoid repeated alerts for a specific value set in throttling_field. Default is 0. Optional.
Incident Condition Parameters
Field
Type
Description
condition_option
string
Must be one of: greaterthan, equals, lessthan, greaterthanorequals, moreequal, lessequal, notequal. Mandatory.
condition_value
number
Threshold value for the condition. Mandatory.
risk
string
Must be one of: low, medium, high, critical. Mandatory.
aggregate
string
Must be one of: max, min, avg. Mandatory.
Taxonomy Parameters
Field
Type
Description
attack_tag_hashes
array of strings
List of MITRE ATT&CK tag identifiers (hashes) linked to this alert rule. Optional.
logsources
array of strings
List of log sources related to the rule. Optional.
metadata
object
Additional metadata as key-value pairs for categorization. Provide objects with field and value. Optional.
Incident Ownership Parameters
Field
Type
Description
assignee
string
Logpoint Username to whom the incidents are assigned. Mandatory.
visible_to_usergroups
array of strings
Names of Logpoint User Group. They must be added to the Incident User Group. Optional.
Incident Display Data Parameters
Field
Type
Description
apply_jinja_template
boolean
Use a custom Jinja template to format the incidents. Default is false. Optional.
simple_view
boolean
Use a simplified layout when displaying this alert. Default is false. Optional.
jinja_template
string
Jinja template string for customizing incident display. Optional.
Four Eyes Parameter
Field
Type
Description
original_data
boolean
If true, includes raw logs in the alert rule for review. Default is false. Optional.
Request Example:
Success and validation error responses:
Editing Alert Rules using API
To edit alert rules, use AlertRules/update_api.
Endpoint URL
https://Logpoint-IP/AlertRules/update_api
Method
POST
Request Headers
Content-Type:
application/jsonAuthorization:
Bearer <TOKEN>
You must include the same parameters as Creating an Alert Rule, and add the alert rule id to update the alert rule information.
Field
Type
Description
Request example:
Success and validation error responses are the same formats as Creating an Alert Rule (HTTP 200 for success, 422 for validation error).
Activating Alert Rules using API
To activate alert rules, use AlertRules/activate_api.
Endpoint URL
https://Logpoint-IP/AlertRules/activate_api
Method
POST
Request Headers
Content-Type:
application/jsonAuthorization:
Bearer <TOKEN>
Parameters
Include parameters in the request body as raw JSON.
Field
Type
Description
Request example:
Success response:
Validation error response:
Deactivating Alert Rules using API
To deactivate alert rules, use AlertRules/deactivate_api.
Endpoint URL
https://Logpoint-IP/AlertRules/deactivate_api
Method
POST
Request Headers
Content-Type:
application/jsonAuthorization:
Bearer <TOKEN>
Parameters
Field
Type
Description
Request Example:
Success Response:
Validation error response:
Deleting Alert Rules using API
To delete alert rules, use AlertRules/delete_api.
Endpoint URL
https://Logpoint-IP/AlertRules/delete_api
Method
POST
Request Headers
Content-Type:
application/jsonAuthorization:
Bearer <TOKEN>
Parameters
Field
Type
Description
Request Example:
Success Response:
Validation error response:
Listing Alert Rules using API
To list alert rules, use AlertRules/lists_api.
Endpoint URL
https://Logpoint-IP/AlertRules/lists_api
Method
GET
Request Header
Authorization:
Bearer <TOKEN>
Parameters
Parameters are sent as query parameters (Key and Value).
Field
Type
Description
limit
integer
Number of alert rules to display. Default is 25. Optional.
page
integer
The alert rule page to display. Default is 1. Optional.
return_all_data
boolean
Whether to display all alert rules. Default is false. Optional.
Request example
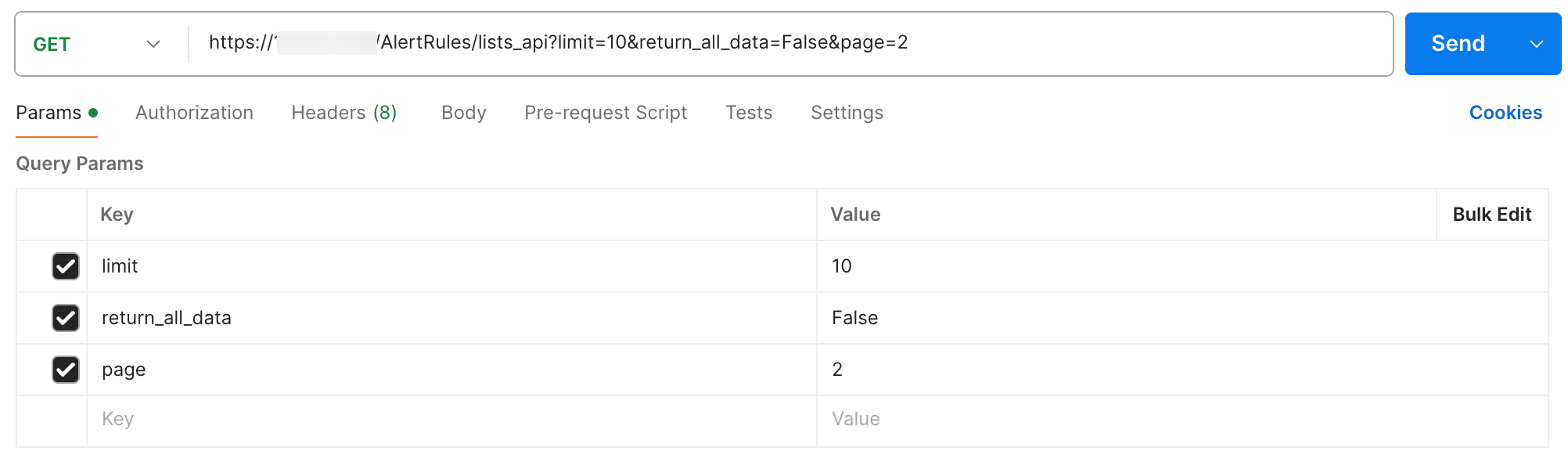
Success response:
Viewing an Alert Rule using API
To view an alert rule, use AlertRules/read_api.
Endpoint URL
https://Logpoint-IP/AlertRules/read_api
Method
GET
Request Header
Authorization:
Bearer <TOKEN>
Parameters
Parameters are sent as query parameters (Key and Value).
Field
Type
Description
Request example:
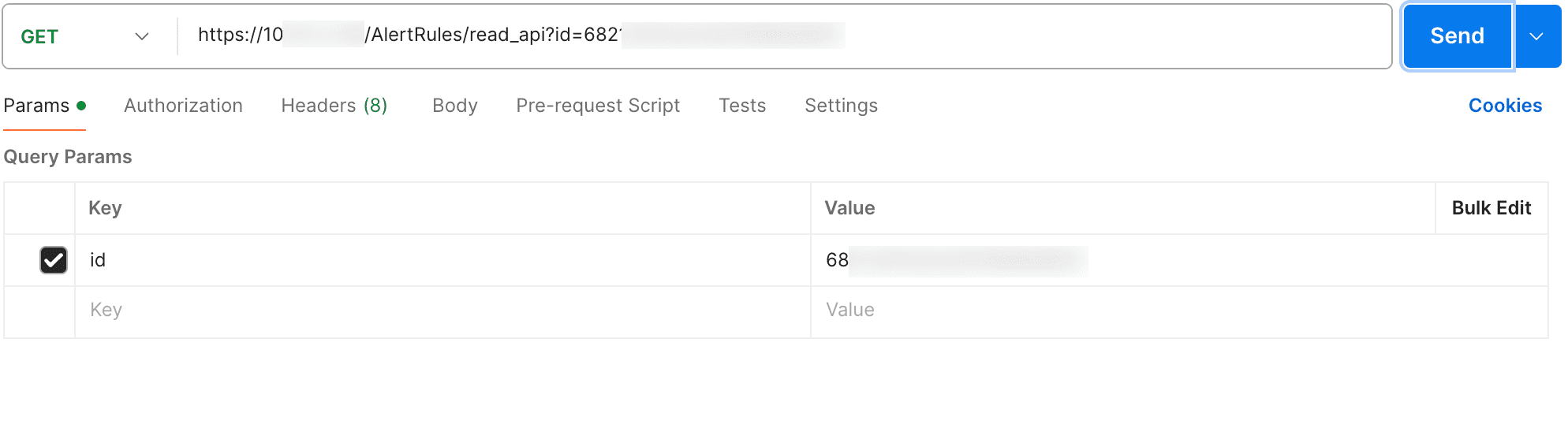
Success response:
Was this helpful?